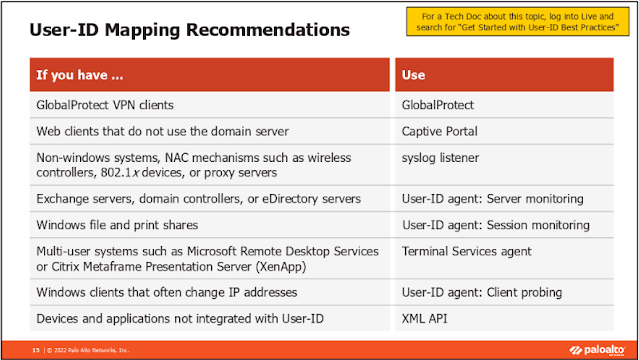
User ID:
AD user agent
LDAP user agent
captive portal
TS agent
PAN client
Configure LDAP
1. Create a service account called "ldap" in AD Managed Service Accounts OU.
2. Verify FW DNS is configured with internal AD/DNS server.
3. Verify Service route for DNS/LDAP points internal LAN.
4. Add a LDAP Server Profile and commit the change
5. Verify LDAP connection is good.
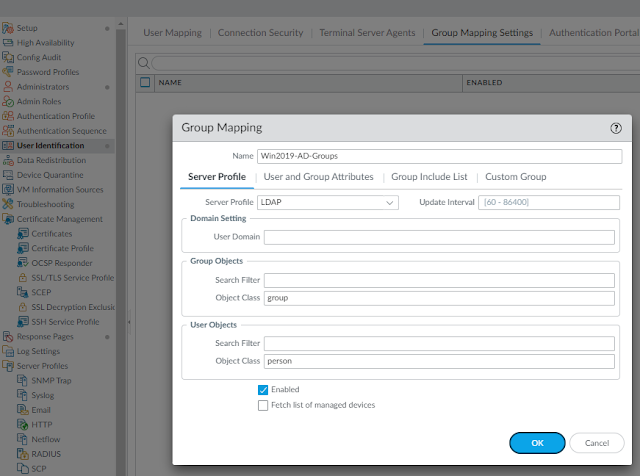
6. Add group mapping, commit the change.
7. Verify Security policy can use username or groups.
Configure User-IP mapping
WinRM is recommenced.
1. Enable User-ID by zone
2. Verify Kerberos service route points to internal and FW DNS is configured with internal AD/DNS server.
3. Create a Kerberos server profile
4. Configure agentless settings.
If use dedicated service account, refer:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/user-id/map-ip-addresses-to-users/create-a-dedicated-service-account-for-the-user-id-agent
5. Add monitor server, commit the change
6. Verify monitor server status is connected
check Logs > User-ID
check mapping from CLI
show user user-ids match-user xxx
show user ip-user-mapping all
admin@PA440-2(active)> show user group-mapping state all
Group Mapping(vsys1, type: active-directory): LDAP-Group-Mapping
Bind DN : cn=ldap,cn=users,dc=sc,dc=local
Base : dc=sc,dc=local
Group Filter: (None)
User Filter: (None)
Servers : configured 1 servers
10.0.0.10(389)
Last Action Time: 3130 secs ago(took 0 secs)
Next Action Time: In 470 secs
Number of Groups: 4
cn=contractors,cn=users,dc=sc,dc=local
cn=employees,cn=users,dc=sc,dc=local
cn=helpdesks,cn=users,dc=sc,dc=local
cn=network admins,cn=users,dc=sc,dc=local
admin@PA440-2(active)> show user group name "cn=network admins,cn=users,dc=sc,dc=local"
User group 'cn=network admins,cn=users,dc=sc,dc=local' does not exist or does not have members
>
admin@PA440-2(active)> debug user-id refresh group-mapping all
group mapping 'LDAP-Group-Mapping' in vsys1 is marked for refresh.
admin@PA440-2(active)> show user group name "cn=employees,cn=users,dc=sc,dc=local"
short name: sc\employees
source type: ldap
source: LDAP-Group-Mapping
[1 ] sc\user1
https://knowledgebase.paloaltonetworks.com/kCSArticleDetail?id=kA10g000000PLey
show global-protect-gateway current-user user xxxx
show global-protect-gateway current-user | match username
Authentication Profile refers a server profile (with Allow List), then be used in creating admin account or captive portal to actually authenticate user:
test authentication authentication-profile Auth-Profile username user1 password
admin@Panorama> test authentication authentication-profile AuthProfielLDAP username user1 password
Enter password :
Target vsys is not specified, user "user1" is assumed to be configured with a shared auth profile.
Do allow list check before sending out authentication request...
name "user1" is in group "all"
Authentication to LDAP server at 172.16.1.10 for user "user1"
Egress: 172.16.1.62
Type of authentication: plaintext
Starting LDAP connection...
Succeeded to create a session with LDAP server
DN sent to LDAP server: CN=user1,CN=Users,DC=lab,DC=local
User expires in days: never
Authentication succeeded for user "user1"
admin@Panorama>
If use local user DB for admin access:
1. Create a local user and/or user group
2. Create a Authentication Profile, authentication type choose Local Database, configure Allow List.
3. Create an administrator identical name with step one, choose Authentication Profile created in step2. Assign Administrator Type Dynamic or Role Based.
If use external DB like radius for admin access:
1. Create Server profile
2. Create Authentication Profile, authentication type choose the one created in spep1.
3. Device>Setup>Management>Authentication Settings, select Authentication Profile created in step 2.
4. Create an Admin Role Profile
Authentication Policy define what trigger the authentication.
=========================
IP-to-User Mappings Have Inconsistent Domain Prefix
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVDCA0
- When show user ip-user-mapping all command is used, some IP-to-user mappings display inconsistent domain prefix
- The inconsistent domain prefix may cause the users listed with the DNS-domain name to hit the wrong security policy, if using group based policies.
- some entries are listed as NetBIOS-domain\username, while others are listed as DNS-domain\username.
- The issue is seen when the domain map is not populated on the device.
- To check for the existence of the domain map run the command, debug user-id dump domain-map. No output is an indication of the problem as it is required to resolve the DNS to NetBIOS domain name. This resolution is required for the user to IP normalization process.
- The domain map can only be pulled a directory partition from a root domain controller.
Group-Mapping notes
If allow-list in authentication profile is configured with specific group, GP is configured with authentication profile, user can't connect with error "not on allow list", need verify the username has group mapping.
show user user-ids match-user employee1
when user is on allowed group:
admin@pa1> show global-protect-gateway current-user
GlobalProtect Gateway: GW1 (1 users)
Tunnel Name : GW1-N
Domain-User Name : lab\employee1
Computer : DESKTOP-LKAG00B
Primary Username : lab\employee1
Region for Config : 192.168.0.0-192.168.255.255
Source Region : 192.168.0.0-192.168.255.255
Client : Microsoft Windows 10 Pro N , 64-bit
VPN Type : Device Level VPN
Host ID : e3808cec-a01d-43d3-88c9-a61ad916150b
Client App Version : 6.2.4-652
Mobile ID :
Client OS : Windows
Private IP : 172.16.1.15
Private IPv6 : ::
Public IP (connected) : 192.168.2.152
Public IPv6 : ::
Client IP : 192.168.2.152
ESP : removed
SSL : exist
Login Time : Mar.01 11:45:13
Logout/Expiration : Mar.31 12:45:13
TTL : 2591990
Inactivity TTL : 10796
Local Owner: : yes
Request - Login : 2025-03-01 11:45:13.739 (1740847513739), 192.168.2.152
Request - GetConfig : 2025-03-01 11:45:13.866 (1740847513866), 192.168.2.152
Request - SSLVPNCONNECT : 2025-03-01 11:45:13.934 (1740847513934), 192.168.2.152
admin@pa1>
Default Group Mapping setting:
with this default setting, use " show user user-ids match-user xxx" query group, if user is sAMAccountName format, group membership returns:
admin@pa1> show user user-ids match-user employee1
User Name Vsys Groups
------------------------------------------------------------------
lab\employee1 vsys1 cn=employees,cn=users,dc=lab,dc=local
cn=gp-vpnusers,cn=users,dc=lab,dc=local
Total: 4
* : Custom Group
admin@pa1>
But if username if UPN, no group membership returns:
admin@pa1> show user user-ids match-user employee1@lab.local
User Name Vsys Groups
------------------------------------------------------------------
Total: 4
* : Custom Group
admin@pa1>
However, if switch Primary Username and Alternative Username 1. both username format return groups.
admin@pa1> show user user-ids match-user employee1
User Name Vsys Groups
------------------------------------------------------------------
employee1@lab.local vsys1 cn=employees,cn=users,dc=lab,dc=local
cn=gp-vpnusers,cn=users,dc=lab,dc=local
Total: 4
* : Custom Group
admin@pa1> show user user-ids match-user employee1@lab.local
User Name Vsys Groups
------------------------------------------------------------------
employee1@lab.local vsys1 cn=employees,cn=users,dc=lab,dc=local
cn=gp-vpnusers,cn=users,dc=lab,dc=local
Total: 4
* : Custom Group
admin@pa1>
admin@pa1> show global-protect-gateway current-user
GlobalProtect Gateway: GW1 (1 users)
Tunnel Name : GW1-N
Domain-User Name : lab\employee1
Computer : DESKTOP-LKAG00B
Primary Username : employee1@lab.local
Region for Config : 192.168.0.0-192.168.255.255
Source Region : 192.168.0.0-192.168.255.255
Client : Microsoft Windows 10 Pro N , 64-bit
VPN Type : Device Level VPN
Host ID : e3808cec-a01d-43d3-88c9-a61ad916150b
Client App Version : 6.2.4-652
Mobile ID :
Client OS : Windows
Private IP : 172.16.1.15
Private IPv6 : ::
Public IP (connected) : 192.168.2.152
Public IPv6 : ::
Client IP : 192.168.2.152
ESP : removed
SSL : exist
Login Time : Mar.01 12:07:37
Logout/Expiration : Mar.31 13:07:37
TTL : 2591980
Inactivity TTL : 10797
Local Owner: : yes
Request - Login : 2025-03-01 12:07:37.402 (1740848857402), 192.168.2.152
Request - GetConfig : 2025-03-01 12:07:37.484 (1740848857484), 192.168.2.152
Request - SSLVPNCONNECT : 2025-03-01 12:07:37.570 (1740848857570), 192.168.2.152
admin@pa1>
Monitor > User-ID, look at the user log if "Group Found" is checked, which means found group.
use >show user user-attributes user domain\user to see if your SAML username is listed there
SAML User Group Attribute
LDAP Group Note 2
1. LDAP server profile is configured and working.
2. No User Identification (Group mapping) is configured
user query group doesn't return group because group mapping is not configured.
3. Add Auth Profile using LDAP server, Advance List > allow list, only "all" is available.
4. User Identification is configured, point to LDAP server, but no Include list, then all AD groups are available in auth profile or firewall rules.
CLI see all the groups the users belongs to
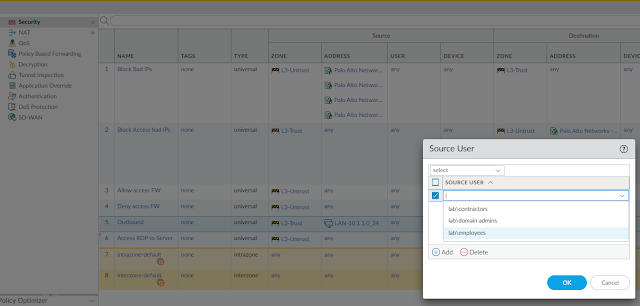
5. Configure Include list in Group Mapping
The auth-profile allow list no longer see other groups are available.
Security rule also has Included group listed
Cli also only listed Included Group



















Comments
Post a Comment