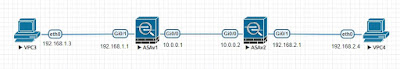
IKEv1 TS 2 - IKE version mismatch
Group Policy VPN protocol mismatch, responsder is configured with IKEv2 only Phase 1 actually is completed, but show crypto isakmp sa doesn't display anything on both initiator and responder. Negotiation failed at QM. Only responder debug gives real reason. I nitiator: Buffer log: Jan 20 2020 15:35:04: %ASA-3-713902: Group = 10.0.0.2, IP = 10.0.0.2, Removing peer from correlator table failed, no match! Jan 20 2020 15:35:04: %ASA-4-113019: Group = 10.0.0.2, Username = 10.0.0.2, IP = 10.0.0.2, Session disconnected. Session Type: LAN-to-LAN, Duration: 0h:00m:00s, Bytes xmt: 0, Bytes rcv: 0, Reason: User Requested Jan 20 2020 15:35:04: %ASA-4-752012: IKEv1 was unsuccessful at setting up a tunnel. Map Tag = MAP. Map Sequence Number = 10. Jan 20 2020 15:35:04: %ASA-3-752015: Tunnel Manager has failed to establish an L2L SA. All configured IKE versions failed to establish the tunnel . Map Tag= MAP. Map Sequence Number = 10. Debug ASAv1# Dec 23 17:59:13 [IKEv1 DEBUG