Firepower, SGT, SXP
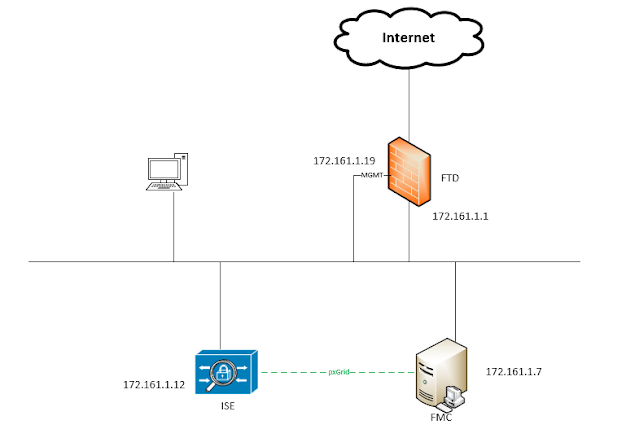
Terminology: SGT - Security Group Tag SXP - SGT Exchange Protocol over TCP EPS - Endpoint Protection Service ANC - Adaptive Network Control TrustSec = Group-Based Policy = Adaptive Policy Security Group = Scalable Group Security Group ACL = Contracts Lab: ISE3.0, FMC/FTD 7.0.5 Pre-requisite: FMC pxGrid to ISE is already configured. Note Session Directory Topic have three ISE services subscribed before SXP Topic is enabled on FMC FMC, enable SXP Topic ISE: enable SXP service ISE: Enable SXP binding on PxGrid Add SXP Devices Seems as long as something is list here is fine, doesn't have to be something configured for FMC Create a Security Group Create a Authorization rule to apply Security Group FMC: Create ACP rule to match source SGT Verification: ISE: FMC: root@fmc67:/var/sf/user_enforcement# uip_reader -f sxp_log_entries.1 -b current set of sxp bindings ipPrefix 172.16.1.203/32, tag 16 ************************************* FMC connection event shows connection hit Test-SG
