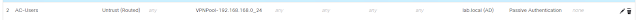
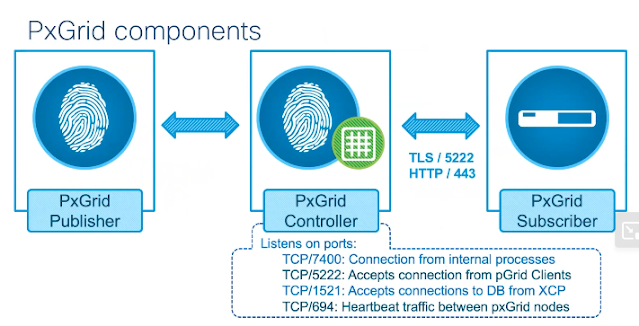
Note: Firepower uses identity policies to detect the user associated with a connection (IP address). An user connects to Anyconnect is a special active authentication, an identity rule matches Anyconnect traffic is required, regardless of active or passive action selected. If there is no identity rule for AC traffic, FMC/FTD will not try to identify the traffic owner, thus won't match any use-id base ACP rules. when identity policy has a rule matches Anyconnect traffic, and VPN is using LDAP for authentication. FMC has an active session when AC user connected when VPN is using ISE for authentication, user shows as Discovered Identity, FW doesn't map user-ip properly, to fix it, need user to put username format lab\user1 or lab.local\user1 uss When ISE is running 802.1x, setup pxGrid between ISE and FMC to pass authentication session info to FMC, in this case, from FMC standpoint, 802.1x is Passive authentication. with 802.1x, machine authentication session is sent to FMC firs