Platform Exchange Grid (pxGrid)
pxGrid is a protocol framework that defines the control mechanisms to facilitate machine-to-machine communications.
pxGrid can synch active ISE session to FMC without ISE-PIC.
ISE-PIC 3.1 only supports pxGrid v2, FMC 6.4 on pxGrid v1, FMC 6.7 and above are on pxGrid v2.
1. Notes:
User Agent is deprecated from FMC 6.7, ISE or ISE-PIC now provides username-IP mapping.
Eligible Firepower Management PIDs for free ISE-PIC
L-FMC-ISE-PIC= (PAK based for ISE-PIC 2.7 and lower)
L-FMC-ISE-PIC-BSE
Smart License Enabled for ISE-PIC 3.0
Standard ISE-PIC PIDs:
● Base license for up to 3,000 user sessions (R-ISE-PIC-VM-K9)
● Upgrade license for up to 300,000 user sessions (L-ISE-PIC-UPG=)
Maximum amount of nodes in ISE PIC deployment is 2.
In an ISE PIC deployment, nodes can have roles: Primary and Secondary. In this only one node can be Primary at a time and roles can only be changed manually through GUI. In case of Primary failure all features still run on Secondary except for UI. Only manual promotion to Primary enables the UI.
WMI
ISE PIC uses Windows Management Instrumentation (WMI) to collect information about sessions from AD and acts like a Pub/Sub communication, which means:
- ISE PIC subscribes to certain events
- WMI alerts ISE PIC when those events occur:
- 4768 (Kerberos Ticket Granting) and 4770 (Kerberos Ticket Renewal)
- Entries in Session Directory expire (Purge)
Agent
(ISE-PIC) Agent that was introduced in the ISE 3.0 version
EVT or Eventing API, which is more efficient . It is sometimes referred to as MS-EVEN6, also known as Eventing Remote Protocol, which is the underlying RPC-based on-the-wire protocol.
Two agents can be installed on DC or member server, they work on Active/Standby mode.
Agent can be manually (Register Existing Agent) or automatically (Deploy New Agent.) installed on the servers
Then when configure Passive ID Domain Controller, we can choose monitoring using Agent or WMI.
The agent and its associated files are installed at the following path: Program Files/Cisco/Cisco ISE PassiveID Agent
A config file called PICAgent.exe.config is installed indicating the logging level for the agent. You can manually change the logging level from within the config file.
The CiscoISEPICAgent.log file is stored with all logging messages.
The nodes.txt file contains the list of all nodes in the deployment with which the agent can communicate. The agent contacts the first node in the list. If that node cannot be contacted, the agent continues to attempt communication according to the order of the nodes in the list. For manual installations, you must open the file and enter the node IP addresses. Once installed (manually or automatically), you can only change this file by manually updating it. Open the file and add, change or delete node IP addresses as necessary.
https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/216512-configure-evt-based-identity-services-en.html
Configuration
1. Add AD as a Provider (ISE-PIC joins to domain )
Providers > Active Directory > Add
2. Add Passive ID Domain Controllers using WMI, "Config.WMI" will make automatic change on DC.
2.1 Providers > Active Directory, edit the added AD
2.2 PassiveID > add the domain controller (DC).
Go to Work Centers > PassiveID > Dashboard to verify PROVIDERS icon is green
3. Prepare FMC certificate PxGrid connection
3.1 import ISE pxGrid root certificate
Objects > PKI > Trusted CAs, import corporate internal CA root cert or ISE internal root certificate depends on which certificate is used for pxGrid service.
3.2 Generate a FMC certificate, this can be issued by corporate internal CA or ISE internal root CA.
CSR can be generated from FMC CLI (Appendix 1) or ISE pxGrid client management > certificate (Appendix 2)
4. Import certificate used for FMC as pxGrid client.
Objects > PKI > Internal Certs, "Add Internal Cert"
===========
5. Configured FMC as pxGrid subscriber
Settings > Integration > Identity Sources > Identity Services Engine
The three CA certificates chain need be import into FMC, can be download from ISE:
Work Centers > PassiveID > Subscribers > Client Management > Certificates > "Download Root Certificate Chain"
In LM video, it is only pxGrid root need be imported to FMC
Note:
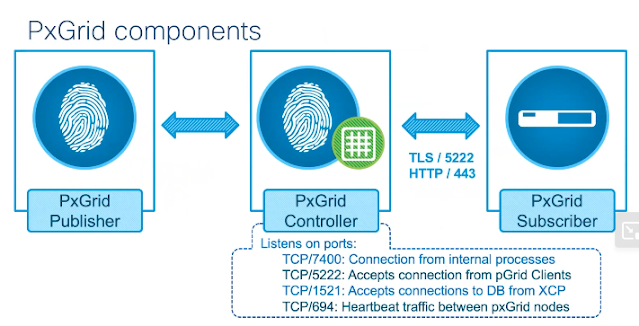
FMC 6.7+ and ISE3.1+ are on PxGrid v2 using port 8910, older PxGrid v1 is on port 5222
6. when FMC successfully Connects to ISE pxGrid, two pxGrid clients can be seen on ISE, the first one is the test connection.
7. Verify username-IP mapping
ISE --Work Centers >PassiveID > Overview > Live session.
FMC -- Analysis > Active sessions
=====Appendix 1=====
Generate new key pair and CSR from CLI.
admin@fmc65:~$ openssl genrsa -out fmc.key 2048
Generating RSA private key, 2048 bit long modulus
.....
............
e is 65537 (0x10001)
admin@fmc65:~$ openssl req -new -key fmc.key -out fmc.csr
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Code []:CA
State or Province Name []:ON
Locality Name []:Toronto
Organization Name []:ISEPICLAB
Organizational Unit Name []:
Common Name []:fmc.isepiclab.local
Email Address []:
admin@fmc65:~$
admin@fmc65:~$ cat fmc.csr
-----BEGIN CERTIFICATE REQUEST-----
MIICozCCAYsCAQAwXjELMAkGA1UEBhMCQ0ExCzAJBgNVBAgTAk9OMRAwDgYDVQQH
EwdUb3JvbnRvMRIwEAYDVQQKEwlJU0VQSUNMQUIxHDAaBgNVBAMTE2ZtYy5pc2Vw
aWNsYWIubG9jYWwwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCTTCky
0KIWlLJ/3W6Ewf70CMBu2uUYsA3Q/zIlVF4otUNGB5RWdXFL8/DrmPmgE0HKD4lz
VnZ6/e++U7TysIVeJRCA+X2Ysgk9zPOKi2E8/O66Z+oWv99mevnbNAhLd/EJAIyg
F9cbFHEhvAtgG/ba09o9msxSd+F6OlTxjt1vnW6+ck0KMPrkorKBOtkicaKqeVjc
QS/NiYbL5b3LudX0xNKcaRQbERa3SNIMQqZ9fuvYizl+rb6n1bS7ONqsRrh1OkwR
Oxy7Ns09ZHZ/sNw00bQMFApEh3TMNn+NnNiHWBdpwPog7MDxuFkI0J1/0m8kipBD
mY8jGnXkQsJW2vDxAgMBAAGgADANBgkqhkiG9w0BAQsFAAOCAQEAfCQHJ5rNkL0o
SZmu1OhQ7OvvREUNfpMewN3DkKASM4XDnkmipsnjD9cIv+fh+ySzyaGNhfqoEqfw
diVZLqanZsocEleqn2dOyS4RI96kgd4p1MqnKR019i4cHcn93vsGk9/V2IMgqCQY
yl71sShUhuAkv0chV0gC++lwZqObGJwDFvfqAPkRfImBKIhDwreMxvbtYl5F3tKQ
omUmkWlyrpNeuE51PRfwrrVRbe86XXEAW09l4sNtst5uvV+X9TR8ej8T4MBvXG5K
6UDwLDBO5Zv4nNUhl0ZR/WmmmPKrpOBhcpKvtkHTVdhasqkH40mXlwNT27VU+pMR
IpJncDidCw==
-----END CERTIFICATE REQUEST-----
-----BEGIN RSA PRIVATE KEY-----
MIIEoQIBAAKCAQEAzF14phkpl3EWj0F4m1Xc9wo4/72Ibu+UEhLsV+OwxbsY1iY+
Tq715xRyP7HFFCMi3Zybdcb2hRyINJQukdNWnBx6svtHYyx64taMp6pq/eT9BZIL
mESlHcu0gSwPhxovwVT92LIO4on19FDhwY2QqLm7HQVHOedFdAZ83ZCujqWv/XMZ
RIXNxHFM0nsVNrgqqxsJDkiDM1RcstVh53jfnJpQSxmqwKPBzKzE/Ki0bcAcsbNI
/nTiln6pj0OMCg1ckxJIy4lULcp2x9kT+SZpt8yby/2kSuhBDIpzQhWtw86ZcA2P
yJT+NNQ5rMXM0QaPoxBw+pc1btcZC0iFrRyMrwIDAQABAoH/fu2PAZqfOnACkvcW
8WNi2gx/WlddZYlnbdJS+ENyh1ytEFSwXi5MjDkmvGis/tTT0tBxvbTVZ9dQwVdH
lUqtgEgv7PokXHRD3p9ivMAbs5WFkPAkQ25fHyJl+dRj0IVzI6CmCPCOTiVhnVye
2pgSQLkafevJUS1S9b0R0IsL34vrUE8eplXg6Zu5yNlYRMWOF0nYTDea0ciQ3qCG
EOh6WRb0GTRL4MyxSTsF7WMkPhpFUvcHoTTHihiqnv4tTwfZ0o0dmCRsfyzyKTxn
DOp3ypSne/arYRjnM6ktBmhsfMCbMMdOsStc1OB4RQ94o6iELUeccRcT4sjfXe2A
xZHRAoGBAPvemax2u1JOCqSC8yatuRpojwgoqxIhnoVoKEDz36hN/B/f77Nd043/
mFcaIF/dJZ0ZV9TmAHUpqWZ12qCKsxbcgNeTwAM9cch3AsHWJxdUfnzs3O/NawaO
wdC5gfSVQqNjYisyNDnuwqYYx+hDV2S6WGRm+rhIYwEnGtXIGLXJAoGBAM+3cBK0
6DkM9okWQOF3GRvAYj6+35x7WXJqkR/V7BBA0tXzw+WK6QtpYTbje1bFV6jFDzX0
p0pp0BmxTd+9z4zK2f6rS7O72/5G4ks8PuPD1KYDKh4zzUbj63K8xOmnBJC1G0ut
wuR5NIM9zgIEntECzu5vD5O6zQkoH2fs8sq3AoGAHP0u5Mm5n6x5zxt/TulZz69P
HxpHLkwOSb6GO4uWJ3HqXeTRWuymp8ZOS2Anb8EtThqXoFpknReRdsiDxEySdkQk
1CseQ4Ez8mW4PIUgdK/16vz8JOGYuuV9az+etH7lb5bFusEJf816O9HIWHQ/v8ku
2Ud8/e7e7kgI76gbJ/kCgYBDcI1kpXPYQgsxSxZZna97QSUkthgn2CycZ1ki+vOf
+0v4xyJNPqKXX+l+RrFe5MenNgPQQtSl5mD4VoawJBJk5d+NPdRgUJgGoMEMKE1K
6eP62oAsOill4M4q/Hr6WY2z5fkswwfJ4khYbBKcuR9PQRgqdcia8EVtuacouNfD
VQKBgQC7yDigahhxKLCnsXFuqUroe46dcxI29LXfeLcPGjE78cmzzuqcwQnHgpT5
1Yu60WJQk4I2X4h/9cE3wayePqTGEgliKuEMOe7D+nHgUyh/jWoszHseczfYnOGA
8pfhGz2xg411DWdohzd90e/BIaGPeczAGoGcmr78ad3H0pr/rQ==
-----END RSA PRIVATE KEY-----
=====Appendix 2======
ISE Internal CA certificates hierarchy used by pxGrid
In two nodes deployment, the first Node is the only internal root CA:
Certificate Services Root CA - ISE30-A
>> Certificate Services Node CA - ISE30-A
>> Certificate Services Endpoint Sub CA - ISE30-A
>> ISE30-A.lab.local
>> Certificate Services Node CA - ISE30-B
>> Certificate Services Endpoint Sub CA - ISE30-B
>> ISE30-B.lab.local
======Appendix 3======
Corporate Internal CA issued pxGrid client certificate
Certificate for pxGrid must contain both client and server authentication in the Extended Key Usage (EKU) extension.
1. Certificate Template > right click > Manage, Create pxGrid certificate template by copying an existing certificate template.
2. Rename new certificate template as "pxGrid", in Subject name tab, select
"Supply in the request".
3. Certificate Template > right click, New > Certificate to issue > select pxGrid
4. pxGrid will show up as a new template in drop down list when request new certificate.
===Appendix 4 ======
Script run on FMC or FTD to check user-ip mapping
user_map_query -u <username>
user_map_query -i <ip_address>
https://www.ciscozine.com/configure-cisco-ise-passiveid/
https://www.ciscozine.com/cisco-fmc-ise-pic-pxgrid/
=========Notes=============
Cisco pxGrid uses a pub/sub model, and publishes ISE contextual information. In addition, pxGrid publishes this session directory topic and other ISE topics of information for ecosystem parters to consume.
Initially pxGrid was released with ISE 1.3 and was XMPP-based, requiring an SDK containing the Java and C libraries, and sample code.
pxGrid 2.0 uses WebSocket and REST API over STOMP (Simple Text Oriented Message Protocol) 1.2 messaging protocol. WebSockets and STOMP are widely used in the industry. WebSockets allow the client and server to keep an open connection, so there is bi-directional communication as opposed to using long polling to keep the connection as was used in hacks prior to using WebSockets. STOMP is used over WebSockets to communicate with any STOMP message broker.
Consuming Session Topic information from ISE
Cisco Identity Services Engine (ISE) contains contains a wealth of session information that ecosystem partners can use in their security policy information. This session information provides user identity information and includes connection type, endpoint device and compliant attributes and more.
=======issue==========
Got error when connect WMI to DC, following log shows in Server log
The server-side authentication level policy does not allow the user AccountID SID (S-1-5-21-3490926982-1646796591-3840444806-2418) from address Your IP to activate DCOM server. Please raise the activation authentication level at least to RPC_C_AUTHN_LEVEL_PKT_INTEGRITY in client application.
Cause:
Windows updates
Solution:
you can use the following registry key:
Path : HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Ole\AppCompat
Value Name: "RequireIntegrityActivationAuthenticationLevel"
Type: dword
Value Data: default = 0x00000000 means disabled. 0x00000001 means enabled. If this value is not defined, it will default to enabled.
reboot server.
https://hiraniconfigmgr.com/postDetails/278/The-server-side-authentication-level-policy-does-not-allow-the-user
==============Notes============
from passive ID report, seems endpoint probe is 4 hours interval; from online help seems on port 445
Endpoint-probe-check-duration=1 seconds ,Endpoint-probe-check-time-interval-in-hours=4
Endpoints must have network connectivity to port 445, verify Windows Firewall is allowed it.
Manually to probe: :Live session > show Action > Check current user
when an user log off from PC, session is still active on ISE-PIC, guess has to wait probe to remove session from ISE-PIC?
When ISE join to AD, there is option to store credential, that is the account used by endpoint probe.
====================pxGrid & FDM============








Comments
Post a Comment