Note:
Firepower uses identity policies to detect the user associated with a connection (IP address).
An user connects to Anyconnect is a special active authentication, an identity rule matches Anyconnect traffic is required, regardless of active or passive action selected.
If there is no identity rule for AC traffic, FMC/FTD will not try to identify the traffic owner, thus won't match any use-id base ACP rules.
when identity policy has a rule matches Anyconnect traffic, and VPN is using LDAP for authentication.
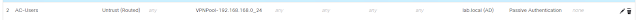
FMC has an active session when AC user connected
when VPN is using ISE for authentication, user shows as Discovered Identity, FW doesn't map user-ip properly, to fix it, need user to put username format lab\user1 or lab.local\user1
uss
When ISE is running 802.1x, setup pxGrid between ISE and FMC to pass authentication session info to FMC, in this case, from FMC standpoint, 802.1x is Passive authentication.
with 802.1x, machine authentication session is sent to FMC first, when the user login, machine authentication session is replaced with user authentication.
same user can login multiple PC
When ISE is not using 802.1x, enable Passive Identity Service to let ISE retrieve login info from AD via WMI or WinRM,
Don't use Passive Identity Service when ISE already have 802.1x. If ISE 802.1x doesn't cover all user authentications to network, deploy separate ISE-PIC for user-ip mapping.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvd73842
====================
Sensor download full file each 5min and make incremental updates on a separate file. So it has two, full, which should be same size as the file on manager, and a small one.
Expert mode command: ls -halt /var/sf/user_enforcement/
---
user_map_query.pl --iu -i 10.7.228.28
user_map_query.pl --iu -u username
---
https://integratingit.wordpress.com/2019/10/26/ftd-user-identity/
https://community.cisco.com/t5/security-knowledge-base/debugging-ftd-identity-based-policy/ta-p/4287436
========
issue 1: FTD doesn't have user group info, FMC has.
user_map_query.pl -u username
Based on the symptoms observed it matched
the following bug, this caveat was initially observed on 6.X codes, as there is
not fixed version yet it is observed to be affecting this version as well
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvr75813
In order to recover the system, the
following commands were entered:
[1] On FM
perl -e "use FlyLoader;
SF::LDAP::signalUGMLisener('0');"
[2] On FTD
pmtool disablebyid SFDataCorrelator
OmniQuery.pl
update estreamer_bookmark set sec=0;
exit
pmtool enablebyid SFDataCorrelator
[3] If FTDs are in HA, repeat steps 2, 2.1 and
2.2 on Secondary FTD
[4] After
this process user_group information must be automatically downloaded to the
FTDs within a few seconds, but you can also Download the user groups under System
> Integration > Realm > Download users and groups to
force an update.
=========================
New lab
1. When there is no identity policy for AC VPN IP address, AC use ISE for authentication and username is vpnuser1, FTD pass the user and IP info to FMC, FMC shows active session with Discovered Identity, since no identity policy, FMC doesn't build user-ip mapping

root@fmc724:~# user_map_query.pl -u vpnuser1
WARNING: This script was not tested on this major version (7.2.5)! The results may be unexpected.
Current Time: 11/24/2023 15:00:54 UTC
Getting information on username(s)...
___
User #1: vpnuser1
---
ID: 20
Last Seen: Unknown
for_policy: 1
==============================
| Database |
==============================
No IP Addresses
##) Group Name (ID)
1) Domain Users (5)
2) VPNUsers (2)
root@fmc724:~#
root@fmc724:~#
root@fmc724:~#
root@fmc724:~#
root@fmc724:~#
root@fmc724:~# user_map_query.pl -i 192.168.100.10
WARNING: This script was not tested on this major version (7.2.5)! The results may be unexpected.
Current Time: 11/24/2023 15:02:04 UTC
Getting information on IP Address(es)...
NOTICE: Unable to get the user info for user_id '10000001'!
___
IP #1: 192.168.100.10
---
==============================
| Database |
==============================
##) Username (ID)
1) (10000001)
for_policy:
Last Seen: Unknown
root@fmc724:~#
To fix this, specify realm in Radius configuration, or use corp/vpnuser1 then login VPN as in next section.
2. When there is no identity policy for AC VPN IP address, AC use ISE for authentication and username is corp\vpnuser1, since FMC has realm corp.local downloaded users and groups, FMC displays user session as below.
If need
root@fmc724:~# user_map_query.pl -u vpnuser1
WARNING: This script was not tested on this major version (7.2.5)! The results may be unexpected.
Current Time: 11/24/2023 15:19:14 UTC
Getting information on username(s)...
___
User #1: vpnuser1
---
ID: 20
Last Seen: Unknown
for_policy: 1
==============================
| Database |
==============================
##) IP Address
1) ::ffff:192.168.100.10
##) Group Name (ID)
1) VPNUsers (2)
2) Domain Users (5)
root@fmc724:~#
root@fmc724:~#
root@fmc724:~# user_map_query.pl -i 192.168.100.10
WARNING: This script was not tested on this major version (7.2.5)! The results may be unexpected.
Current Time: 11/24/2023 15:19:23 UTC
Getting information on IP Address(es)...
___
IP #1: 192.168.100.10
---
==============================
| Database |
==============================
##) Username (ID)
1) vpnuser1 (20)
for_policy: 1
Last Seen: Unknown
root@fmc724:~#
But identity policy is still required, otherwise, it won't enforce traffic based on username even has mapping.
3. Wireless test
PxGrid is established between FMC and ISE32. Wireless user session is synched to FMC. Mapping is seen on FMC/FTD even no identity policy.
root@fmc72:~# user_map_query.pl -u employee1
WARNING: This script was not tested on this major version (7.2.5)! The results may be unexpected.
Current Time: 11/28/2023 17:19:23 UTC
Getting information on username(s)...
___
User #1: employee1
---
ID: 6
Last Seen: Unknown
for_policy: 1
==============================
| Database |
==============================
##) IP Address
1) ::ffff:192.168.2.172
##) Group Name (ID)
1) Domain Users (5)
2) Employees (7)
root@fmc72:~#
root@fmc72:~#
root@fmc72:~# user_map_query.pl -i 192.168.2.172
WARNING: This script was not tested on this major version (7.2.5)! The results may be unexpected.
Current Time: 11/28/2023 17:19:40 UTC
Getting information on IP Address(es)...
___
IP #1: 192.168.2.172
---
==============================
| Database |
==============================
##) Username (ID)
1) employee1 (6)
for_policy: 1
Last Seen: Unknown
root@fmc72:~#
===
Firewall rule location
/ngfw/var/sf/detection_engines/<UUID>/ngfw.rules
# Start of AC rule.
268434433 allow 2 10.1.4.0 24 any 1 any any any any (log dcforward flowend)
# End rule 268434433
268436480 allow 2 192.168.100.0 24 any 1 any any any any (log dcforward flowend) (user 13)
# End rule 268436480
268435456 allow 1 192.168.100.0 24 any 1 any any any any (group 2) (log dcforward flowend)
# End rule 268435456
268435459 allow 4 10.1.3.0 24 any 3 0.0.0.0 0 any any any (log dcforward flowstart)
# End rule 268435459
268434432 deny any any any any any any any any (log dcforward flowstart)
# End rule 268434432
# End of AC rule.
We can see user/group based firewall rules have user or group ID.
When a connection reaches firewall, Firewall will query the IP to find a matching user ID and group ID, then check connection against FW rules






Comments
Post a Comment