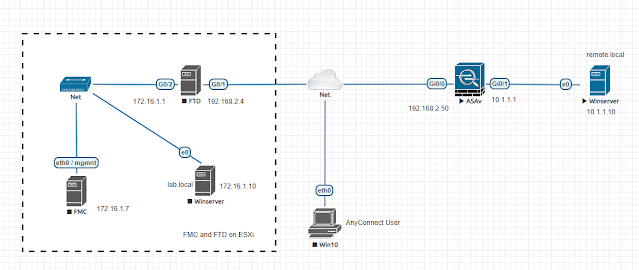
1. Anyconnect DHCP configuration in FMC this is a host object, can be .0 or any number in the scope. 2. Packet capture on DHCP server DHCP discover packet is unicast DHCP offer is unicast to DHCP replay IP, not FW IP. ================== This article says IP-Helper address is required when DHCP server is not on the same subnet with FTD inside interface, but since DHCP packets we saw above are unicast, IP-Helper address shouldn't be required. https://www.cisco.com/c/en/us/support/docs/security/anyconnect-secure-mobility-client/215854-configure-anyconnect-vpn-client-on-ftd.pdf Case: AC client didn't receive IP address, capture on DHCP server had the repeated DHCP Discover and Offer packets , packet tracer showed DHCP offer hit a NAT rule then was sent to outside interface, found the exemption NAT is missing route-lookup keyword caused the DHCP offer wasn't processed as expected .