ISE Admin with AD Credential
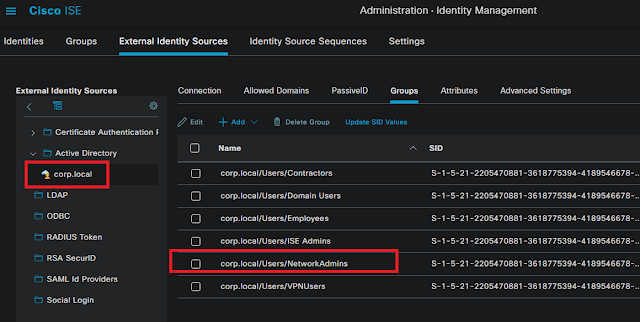
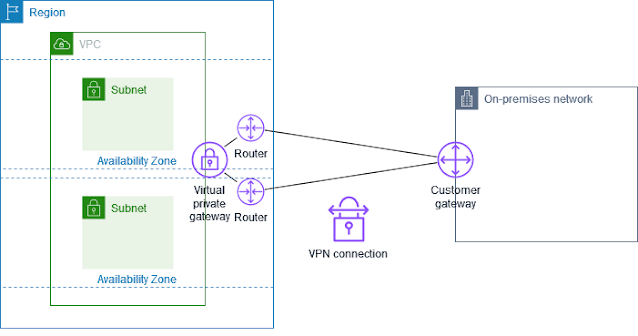
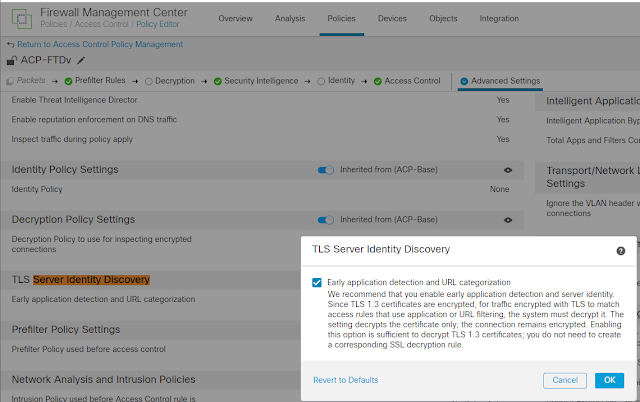
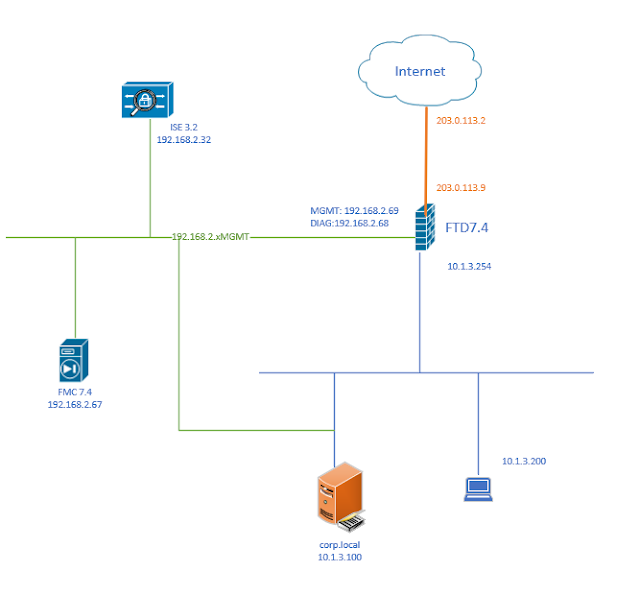
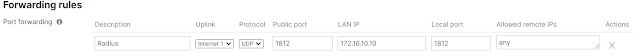
Summary steps 1. ISE join AD 2. Enable admin access using AD 3. Configure Admin Group to AD group mapping 4. Set RBAC permission for the admin group Detail Steps: 1. ISE join AD Assume is already done, joined corp.local domain AD group NetworkAdmins is added to ISE AD group list 2. Enable admin access using AD 3. Configure Admin Group to AD group mapping 4. Set RBAC permission for the admin group Duplicate "Super Admin Policy" , create a new policy "AD Admin Policy" for group "AdminGroup-AD" reference: https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/116503-configure-product-00.html