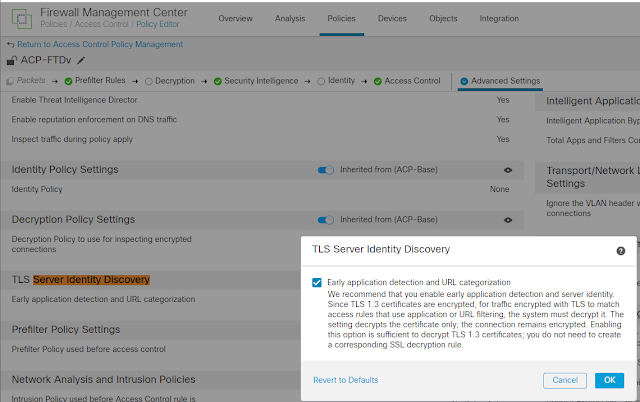
1. TLS Server Identity Discovery
Note: in TLS 1.3 SNI is still cleartext, FTD still can use SNI solely to determine URL or application, but without server side certificate, the confidence and reliability is getting low.
SNI can be spoofed or empty,
New feature (from FTD 6.7) TLS Server Identity Discovery without requiring SSL decryption
Read: Network Security Efficacy in the Age of Pervasive TLS Encryption
https://blogs.cisco.com/security/network-security-efficacy-in-the-age-of-pervasive-tls-encryption?ccid=cc000155&dtid=oblgcdc000651&oid=pstsc023056
FTD intercepts a TLS 1.3 handshake message from a client to an unknown server and then opens a side connection to this server to discover its identity. FTD uses the same source IP address and TCP port as the client and mimics the ClientHello message as much as possible to get the server to present its true certificate. Once the server’s identity is established, FTD applies an appropriate application or URL policy to permit or deny access, or even engage full TLS decryption. It also caches the server’s identity to avoid repeated identify lookups for multiple clients that access the same resource.
FMC 7.4
Encrypted Visibility Engine (EVE).
Elephant Flow Detection
Users can configure three elephant flow detection outcomes:
- Alerting - by adding a note to the Reason field in a connection event.
- Flow bypass* - this can be select for all flows or just flows matching selected application criteria.
- Flow throttling* - flows can be throttled by adjusting TCP window sizes to reduce the flow's CPU usage and prevent consequences such as high latency or packet drops.
Note
* Taking actions on an elephant flow is not supported on Firepower 2100 Series devices.
https://secure.cisco.com/secure-firewall/docs/elephant-flow-throttling
Merge the Management and Diagnostic Interfaces
FTD 7.4 and later supports a merged Management and Diagnostic interface
After merge, the "management" interface is now shown in read-only mode on the Interfaces page.
You can add static routes for the Linux routing table at the CLI using the configure network static-routes command
Before Merge


Comments
Post a Comment