Secure Firewall Posture (Formerly HostScan)
The Cisco Secure Client (AnyConnect Secure Mobility Client) offers a Secure Firewall Posture Module (VPN Posture), formerly HostScan, and an ISE Posture Module. Both provide the Cisco Secure Client with the ability to assess an endpoint's compliance for things like antivirus, antispyware, and firewall software installed on the host. You can then restrict network access until the endpoint is in compliance or can elevate local user privileges so they can establish remediation practices.
Secure Firewall Posture is bundled with secure-firewall-posture-<version>-k9.pkg, which is the application that gathers what operating system, antivirus, antispyware, and software is installed on the host. ISE Posture deploys on client when accessing ISE-controlled networks, rather than deploying both Cisco Secure Client and the NAC Agent. ISE Posture is a module you can choose to install as an additional security component into the Cisco Secure Client product.
ISE Posture performs a client-side evaluation. The client receives the posture requirement policy from the headend, performs the posture data collection, compares the results against the policy, and sends the assessment results back to the headend. Even though ISE actually determines whether or not the endpoint is compliant, it relies on the endpoint's own evaluation of the policy.
In contrast, Secure Firewall Posture performs server-side evaluation where the Secure Firewall ASA asks only for a list of endpoint attributes (such as operating system, IP address, registry entries, local certificates, and filenames), and they are returned by Secure Firewall Posture. Based on the result of the policy’s evaluation, you can control which hosts are allowed to create a remote access connection to the security appliance.
 Note |
The combined use of Secure Firewall Posture and ISE posture agent is not supported. Unexpected results occur when two different posture agents are running. |
1. Download hostscan image, upload it to ASA flash, specify it in webvpn configuration.
ASA#sh run webvpn
webvpn
enable outside
hostscan image disk0:/hostscan_4.10.03104-k9.pkg
!! for secure firewall client 5.0
!! hostscan image disk0:/secure-firewall-posture-5.0.02075-k9.pkg
hostscan enable
anyconnect image disk0:/anyconnect-win-4.10.03104-webdeploy-k9.pkg 1
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
ASA#
ASAv916(config-webvpn)# hostscan image disk0:/secure-firewall-posture-5.0.0207$
WARNING: The existing AV/AS/FW DAP is not compatible with the latest Hostscan version
For FTD:
Object > Object Management > VPN >
2. Enable Anyconnect VPN posture in Group Policy
ASA# sh run group-policy
group-policy GroupPolicy_SSL-VPN internal
group-policy GroupPolicy_SSL-VPN attributes
wins-server none
dns-server value 8.8.8.8
vpn-tunnel-protocol ssl-client
default-domain none
webvpn
anyconnect modules value posture
ASA#
3. Create DAP Policy
3.1 Posture (for Secure Firewall) > Posture Settings, configure basic posture and/or Posture extensions. -- This is to tell posture module what need to scan.
3.2 Create DAP rules to tell ASA what scan result need to be checked, this only works when the 1st step is configured.
4. Enable syslog for troubleshooting
ASA# sh run logging
logging enable
logging timestamp
logging trap notifications
logging host inside 10.10.10.10
logging class dap trap debugging
ASA#
syslog will be like this:
%ASA-7-734003: DAP: User bob, Addr 192.168.2.204: Session Attribute endpoint.am["362"].description="Windows Defender"
default DAP doesn't generate detail host scan log, only manually create new DAP rule generate detail log even new DAP rule is empty.
Note:
Basic Host Scan is only to scan Registry, File and Process.
HostScan Extension can examines antivirus and antispyware
applications, associated definitions updates, and firewalls.
=======================
If you want to check to confirm whether the computer is joined to the domain, locate the domain name in the registry of the computer. E.g:-
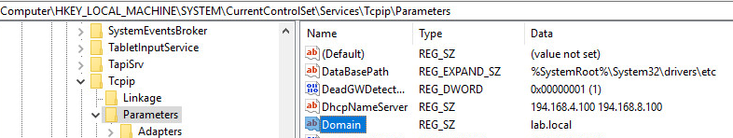
Then create a basic hostscan for that registry value. E.g:-
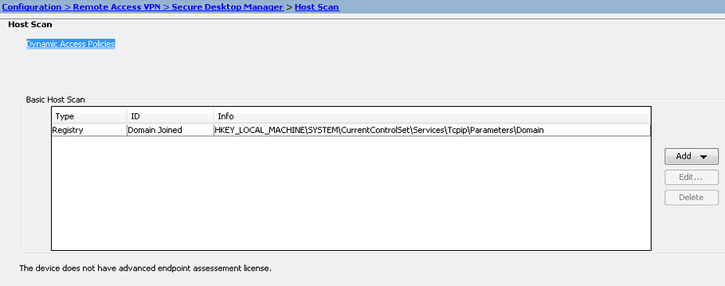
Create a new DAP, define tunnel-group user is connecting from and check endpoint attributes to determine whether the registry value is correct (in this example lab.local is the local domain). Action is continue if matched. E.g:-
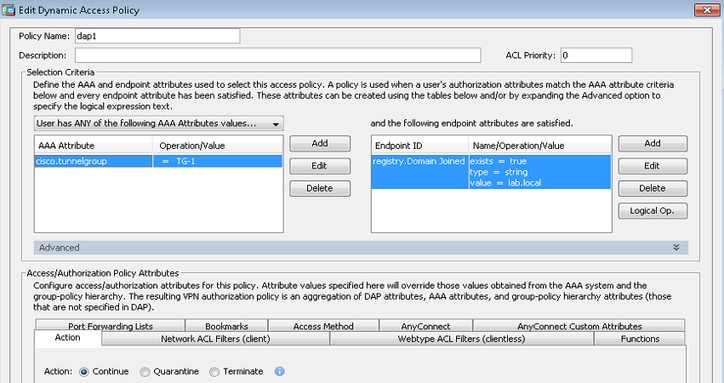
Hostscan on FMC/FTD
https://www.cisco.com/c/en/us/td/docs/security/secure-firewall/management-center/cluster/ftd_dap_usecases.html
https://www.cisco.com/c/en/us/td/docs/security/secure-firewall/management-center/device-config/710/management-center-device-config-71/vpn-dap.html
1. Upload hostscan image
Object > Object Management > VPN > Anyconnect Profile
2. Create a DAP policy and specify the hostscan image.
Devices > VPN > Dynamic Access Policy
3. Edit the created DAP Policy, add DAP Record
4. Associate DAP to a Remote VPN
Devices > VPN > "
remoe vpn name", locate "Dynamic Access Policy" in the right top corner, associate a DAP policy.
5: Logging
6. Verify:
Aug 11 2023 15:09:41: %FTD-7-734003: DAP: User local1, Addr 203.0.113.133: Session Attribute endpoint.anyconnect.platform = "win"
Aug 11 2023 15:09:41: %FTD-7-734003: DAP: User local1, Addr 203.0.113.133: Session Attribute endpoint.anyconnect.devicetype = "VMware, Inc. VMware7,1"
Aug 11 2023 15:09:41: %FTD-7-734003: DAP: User local1, Addr 203.0.113.133: Session Attribute endpoint.anyconnect.platformversion = "10.0.19045 "
Aug 11 2023 15:09:41: %FTD-7-734003: DAP: User local1, Addr 203.0.113.133: Session Attribute endpoint.anyconnect.deviceuniqueid = "C1A2EABE24F2AC1534CB7677D5DA19CF25730F97D0D7D55F8CDDAD6C377EE3B3"
Aug 11 2023 15:09:41: %FTD-7-734003: DAP: User local1, Addr 203.0.113.133: Session Attribute endpoint.anyconnect.deviceuniqueidglobal = "21AC19CF91A508BCE49BA28B9CEFE9EBE75460EB"
Aug 11 2023 15:09:41: %FTD-7-734003: DAP: User local1, Addr 203.0.113.133: Session Attribute endpoint.anyconnect.macaddress["0"] = "00-0c-29-83-65-52"
Aug 11 2023 15:09:41: %FTD-7-734003: DAP: User local1, Addr 203.0.113.133: Session Attribute endpoint.anyconnect.useragent = "AnyConnect Windows 5.0.01242"
Aug 11 2023 15:09:41: %FTD-7-734003: DAP: User local1, Addr 203.0.113.133: Session Attribute endpoint.anyconnect.publicmacaddress = "00-0c-29-83-65-52"
Aug 11 2023 15:09:41: %FTD-7-734003: DAP: User local1, Addr 203.0.113.133: Session Attribute endpoint.anyconnect.session_token_security = "true"
Aug 11 2023 15:09:41: %FTD-6-734001: DAP: User local1, Addr 203.0.113.133, Connection AnyConnect: The following DAP records were selected for this connection: Check-Endpoint
Aug 11 2023 15:09:46: %FTD-4-722041: TunnelGroup <SSLVPN> GroupPolicy <GP-SSLVPN> User <local1> IP <203.0.113.133> No IPv6 address available for SVC connection
Aug 11 2023 15:09:46: %FTD-4-722051: Group <GP-SSLVPN> User <local1> IP <203.0.113.133> IPv4 Address <192.168.100.10> IPv6 address <::> assigned to session
ftd724#
issue
when DAP is attach to Remote VPN policy, on user PC, browsing VPN URL, is directed to Cisco Secure Desktop WebLuanch page, unable to download Anyconnect.











Hi is there any workaround about this issue please? when DAP is attach to Remote VPN policy, on user PC, browsing VPN URL, is directed to Cisco Secure Desktop WebLuanch page, unable to download Anyconnect.
ReplyDelete