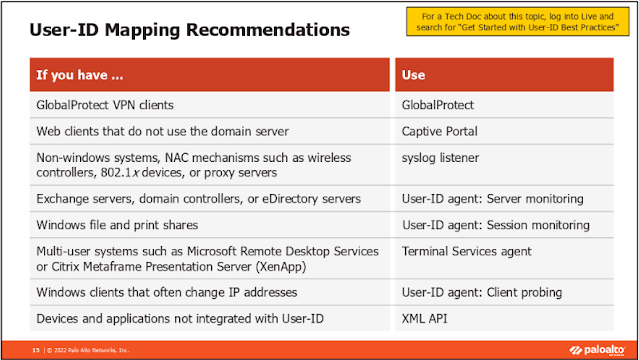
Firepower FTD/ASA: Block Anyconnect brute force attack
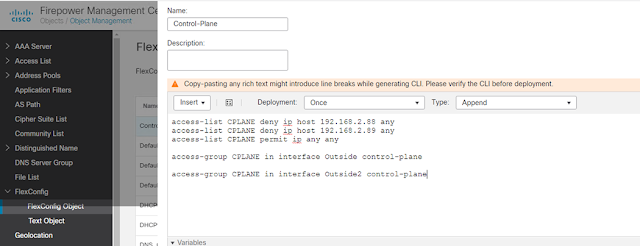
Situation: Attacker attempts to connect Anyconnect, Anyconnect sends authentication to ISE, ISE sends authentication to AD. In ISE logs, there are lots failed Radius requests with non-exist username, AD is overwhelmed, can't process more legitimate AD authentication request. During this attack, ISE normally is not the one get overwhelmed. Anyconnect user's public IP is in Radius attribute calling-station-ID Issue: 1. ISE failed authentication suppression seems only for existing user accounts. 2. FTD /ASA Anyconnect doesn't have the ability to filter source IP geo location. 3. FTD Security Intelligence doesn't block IP to AC 4. FTD Prefilter policy doesn't work. Cisco Enhancement request: https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvs65322?rfs=iqvred Solution: 1. "shun" command on FTD/ADA CLI 2. deny attacker's IP in control plane ACL in appendix 1 3. enable anti-spoof on FW AC interface, create null0 route for attack er's IP. ===========