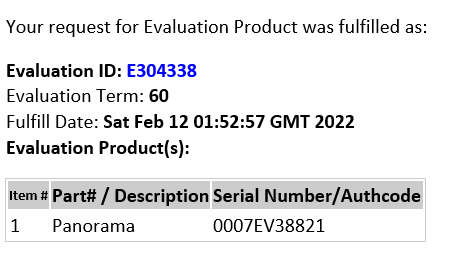
Firepower Disk Usage Troubleshooting
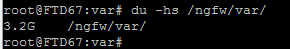
1. Disk manager df-h root@ FTD67 :/# df -h Filesystem Size Used Avail Use% Mounted on rootfs 3.9G 398M 3.5G 11% / devtmpfs 3.9G 12M 3.9G 1% /dev tmpfs 3.9G 1.1M 3.9G 1% /run tmpfs 3.9G 220K 3.9G 1% /var/volatile /dev/sda1 510M 253M 258M 50% /mnt/boot /dev/sda2 8.0G 80M 8.0G 1% /mnt/disk0 /dev/sda6 3.8G 574M 3.1G 16% /ngfw /dev/sda8 28G 6.0G 21G 23% /ngfw/Volume tmpfs 3.9G 0 3.9G 0% /dev/cgroups admin@ fmc724 :~$ df -h Filesystem Size Used Avail Use% Mounted on /dev/sda5 3.7G 1.5G 2.0G 44% / none 16G 0 16G 0% /dev /dev/sda1 87M 16M 64M 20% /boot /dev/sda7 237G 21G 205G 10% /Volume none 16G 128K 16G 1% /dev/shm tmpfs 16G 0 16G 0% /sys/fs/cgroup tmpfs 16G 0 16G 0% /sys/fs/cgroup/pm admin@fmc724:~$ admin@ ftd724 :~$ df -h Filesystem Size Used Avail Use% Mou