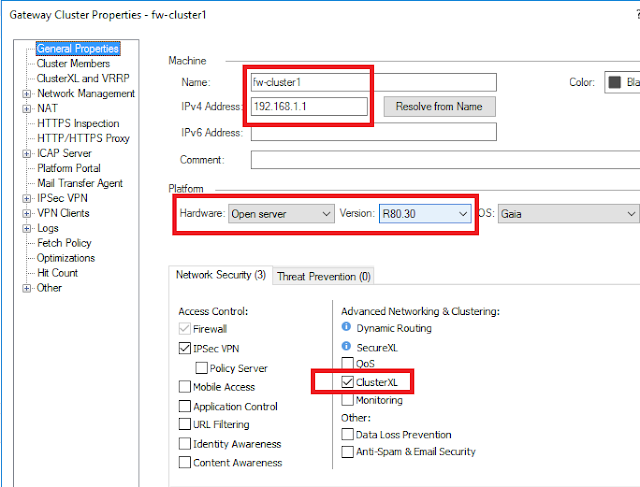
ISE - Wired - Machine and User authentication

In wired NIC Authentication tab, click Additional Settings > Specify Authentication mode Computer authentication --- only computer account is sent to ISE User authentication --- only user account is sent to ISE User or Computer authentication --- when PC boot up or switch port comes up, machine authentication starts first, with successful machine authentication, machine Authorization profile applies; after user login, user authentication starts, with successful user authentication, the new user Authorization profile applies. Computer Dot1X authentication only occurs when the computer boot up and when the user logout, shut /no shut switch port doesn't trigger computer to redo Dot1X authentication, only computer MAB and user dot1x occur. A Common session ID is created after computer authentication, successful user authentication is using the same session ID, on ISE, this is Audit Session ID. MAR. PEAP doesn't allow for the user AND computer to aut