1. Create tunnel interface, IP address is optional
set interfaces st0 unit 0 family inet
2. Assign the tunnle interface to VPN zone,
set security zones security-zone VPN interfaces st0.0
3. Set routing for remote network
set routing-options static route 192.168.1.0/24 next-hop st0.04. Enable ike on outside interface
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services ike
5. Create P1 proposal
set security ike proposal ASA-P1 authentication-method pre-shared-keys
set security ike proposal ASA-P1 dh-group group14
set security ike proposal ASA-P1 authentication-algorithm sha-256
set security ike proposal ASA-P1 encryption-algorithm aes-256-cbc
set security ike proposal ASA-P1 lifetime-seconds 86400
6. Create P1 policy, link the P1 proposal, set pre-share key.
set security ike policy ASA-P1-POLICY mode main
set security ike policy ASA-P1-POLICY proposals ASA-P1
set security ike policy ASA-P1-POLICY pre-shared-key ascii-text Cisco123
7. Create gateway for remote peer, link the P1 policy, specify the interface to reach peer.
set security ike gateway ASA ike-policy ASA-P1-POLICY
set security ike gateway ASA address 203.0.113.1
set security ike gateway ASA dead-peer-detection
set security ike gateway ASA external-interface ge-0/0/0.0
set security ike gateway ASA version v2-only
8. Create P2 proposal
set security ipsec proposal ASA-P2 protocol esp
set security ipsec proposal ASA-P2 authentication-algorithm hmac-sha-256-128
set security ipsec proposal ASA-P2 encryption-algorithm aes-256-cbc
set security ipsec proposal ASA-P2 lifetime-seconds 28800
9. Create P2 policy, link the P2 proposal
set security ipsec policy ASA-P2-POLICY perfect-forward-secrecy keys group14
set security ipsec policy ASA-P2-POLICY proposals ASA-P2
10.Create the VPN, link gateway, P2 policy and tunnel interface.
set security ipsec vpn ASA-VPN bind-interface st0.0
set security ipsec vpn ASA-VPN ike gateway ASA
set security ipsec vpn ASA-VPN ike ipsec-policy ASA-P2-POLICY
set security ipsec vpn ASA-VPN establish-tunnels on-traffic
11. Create security policy for outbound and inbound vpn traffic
set security address-book global address LOCAL-NET-192.168.2.0_24 192.168.2.0/24
set security address-book global address REMOTE-NET-192.168.1.0_24 192.168.1.0/24
set security policies from-zone trust to-zone VPN policy To-ASA match destination-address REMOTE-NET-192.168.1.0_24
set security policies from-zone trust to-zone VPN policy To-ASA match application any
set security policies from-zone trust to-zone VPN policy To-ASA then permit
set security policies from-zone VPN to-zone trust policy From-ASA match source-address REMOTE-NET-192.168.1.0_24
set security policies from-zone VPN to-zone trust policy From-ASA match destination-address LOCAL-NET-192.168.2.0_24
set security policies from-zone VPN to-zone trust policy From-ASA match application any
set security policies from-zone VPN to-zone trust policy From-ASA then permit
============SRX Basic Config===========
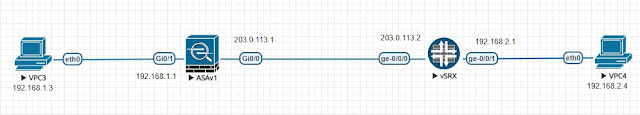
set interfaces ge-0/0/0 unit 0 family inet address 203.0.113.2/24
set interfaces ge-0/0/1 unit 0 family inet address 192.168.2.1/24
set security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system-services ping
set routing-options static route 0.0.0.0/0 next-hop 203.0.113.1
Comments
Post a Comment