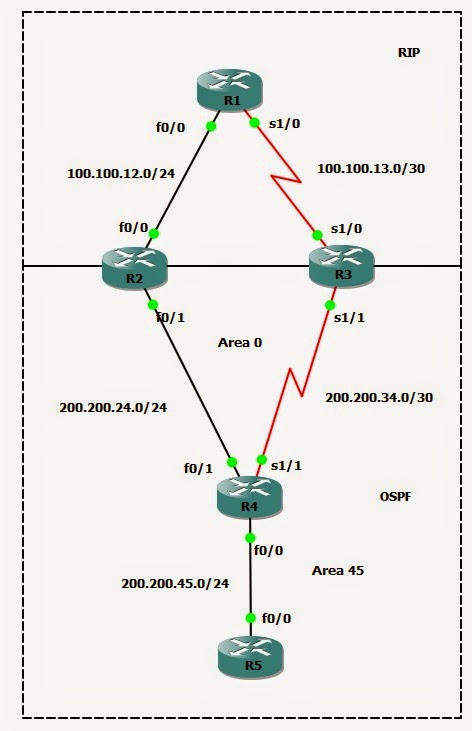
Backbond fast

Backbone fast is a Cisco proprietary feature that, once enabled on all switches of a bridge network, can save a switch up to 20 seconds (max_age) when it recovers from an indirect link failure. Let's shut down SW1 e0/0 to simulate the link failure. SW1(config)#int e0/0 SW1(config-if)#shut SW1(config-if)# *Dec 29 18:26:01.487: %LINK-5-CHANGED: Interface Ethernet0/0, changed state to administratively down *Dec 29 18:26:02.487: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/0, changed state to down SW1(config-if)# SW3(config)# *Dec 29 18:26: 10 .327: STP: VLAN0001 heard root 32769-aabb.cc00.0200 on Et0/0 SW3(config)# *Dec 29 18:26: 12 .323: STP: VLAN0001 heard root 32769-aabb.cc00.0200 on Et0/0 SW3(config)# *Dec 29 18:26: 14 .327: STP: VLAN0001 heard root 32769-aabb.cc00.0200 on Et0/0 SW3(config)# *Dec 29 18:26: 16 .327: STP: VLAN0001 heard root 32769-aabb.cc00.0200 on Et0/0 SW3(config)# *Dec 29 18:26: 18 .327: STP: VLAN0001 heard root 32769-aabb.cc00.0200 on Et0