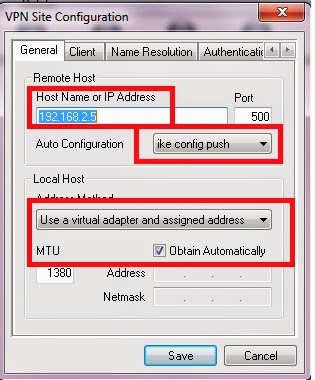
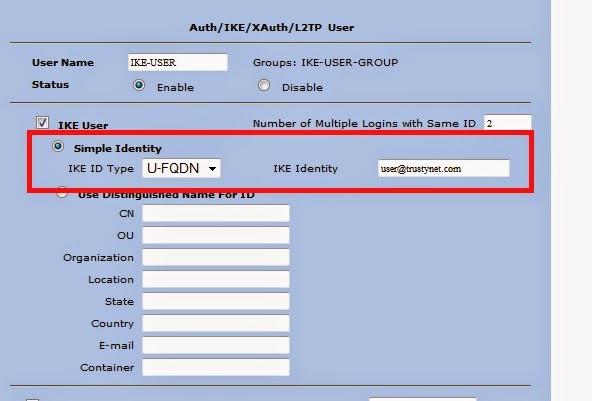
SSG session/flow troubleshooting
1. get session info Home-SSG5-> get session src-ip x.x.x.x dst-ip y.y.y.y alloc 11/max 8064, alloc failed 0, mcast alloc 0, di alloc failed 0 total reserved 0, free sessions in shared pool 8053 id 8048/s**,vsys 0,flag 00000040/0080/0021/0000,policy 320002,time 180, dip 0 module 0 if 0(nspflag 800601):192.168.2.173/4471->192.168.2.5/22,6,902b34859902,sess token 4,vlan 0,tun 0,vsd 0,route 1,wsf 0 if 3(nspflag 2002010):192.168.2.173/4471<-192 .168.2.5="" 0="" 5="" br="" route="" sess="" token="" tun="" vlan="" vsd="" wsf="">Total 1 sessions shown Home-SSG5-> 2. Debug flow basic 1) get ffilter - see if an filters have been set already, if they have you use 'unset ffilter' to remove, repeat the steps until you remove all the filters 2) set ffilter src-ip 10.1.1.5 dst-ip 1.1.70.250 - allows you to limit the traffic that you capture