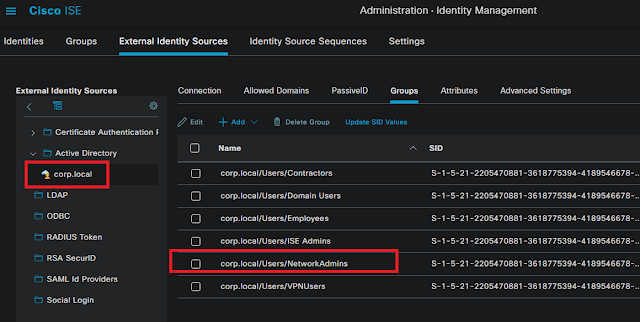
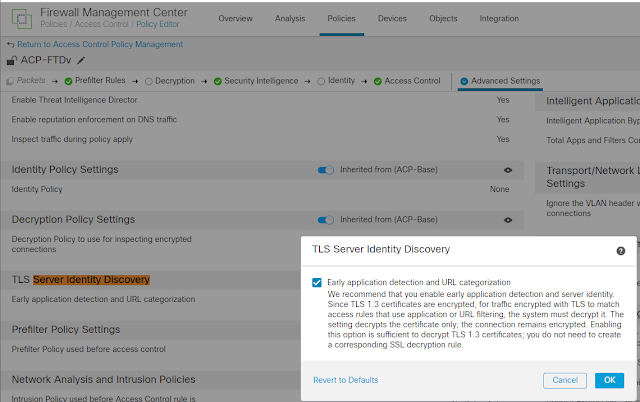
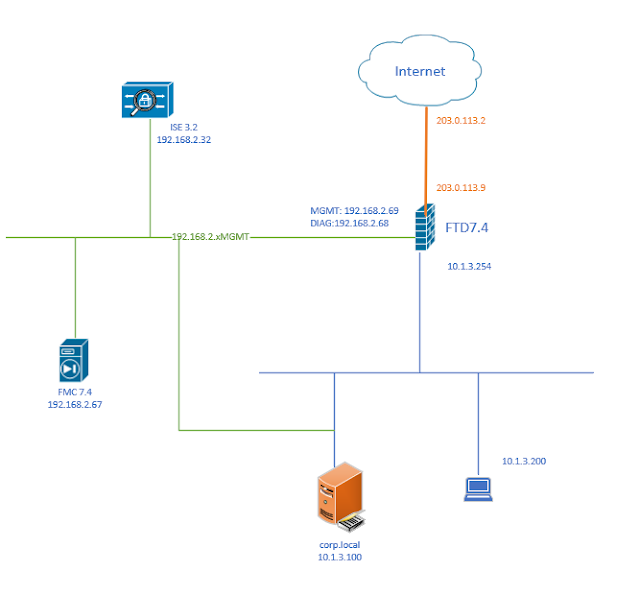
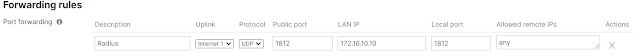
1. Test Result: When SC detects PC is on Untrusted network, it prompts to ask the user to connect to VPN. When SC detects PC is on Trusted network, it doesn't prompt. 2. Enable Always on Test result User can disconnect VPN, but only can access www.google.ca and DNS server 203.0.113.2 When ASA is not reachable, "Connect Failure Policy" kick in, with "Open" policy, user is able to access any websites. When ASA is reachable again, prompt user to connect, at this moment, again, only www.google.ca and DNS server 203.0.113.2 are able to connected. 3. Captive Portal By default, captive portal detection is enabled, as soon the PC connects a Open wifi with Captive portal, Cisco Secure Client - Web Browser is popup, in the lab, it is display a blank page, depends on configurations in profile, the browser window may disappear in a second or stay open. Captive portal detection need be disable if we don't want to see this browser. Windows 10 has internal mecha