Capture on management interface
view-pcap mgmt-pcap mgmt.pcap
scp export mgmt-pcap from mgmt.pcap to admin@192.168.1.1:/
1. Concept
Basic deployment vs Distributed Deployment
Mode:
Panorama mode
Log Collector mode
Management only mode
2. Deployment
Select Thick Provision Lazy Zeroed as the disk format.
Wait for login prompt
Panorama login:
2.1 Old Way: Register the Panorama Serial Number in CSP.
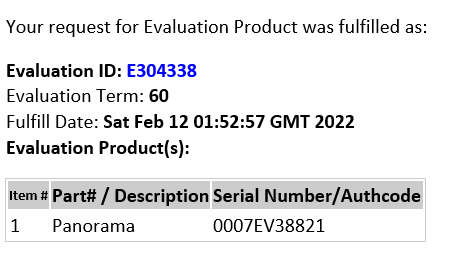
For VM, Serial number is in the email:
In Support Portal Devices list, register received Panorama Serial Number/Authcode,
if VM doesn't have Internet connection, click the Action to download key, then in Panorama license page, click.
Manually upload license key
1. VM only:
Enter the Panorama
2. In license page, click
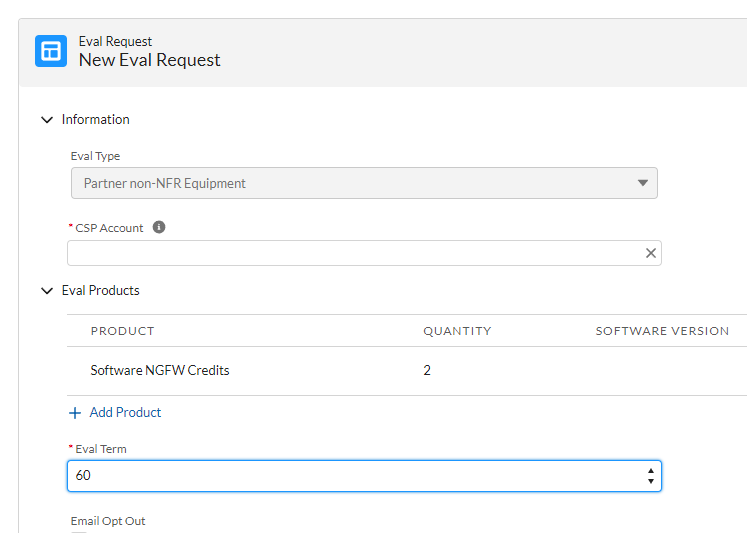
- In received email, click Activate, will be redirected to CSP to create deployment profile.
- Select Products > Software NGFW Credits and click the Details button on the credit pool you used to create your profile.
- On the far right, select the vertical ellipsis (More Options) and select Provision Panorama, and Provision, this will generate Panorama serial number and Auth-Code.
- In newly installed Panorama, first time login will see.
https://docs.paloaltonetworks.com/panorama/10-0/panorama-admin/set-up-panorama/register-panorama-and-install-licenses/activateretrieve-a-firewall-management-license-on-the-panorama-virtual-appliance.html#id5fd6c4c0-1cc7-456d-a959-291b1726cda6
=======Panorama====
Template: Network, Device
Template Stack
by default, template at the top take precedence
Template variable name starts with $
variables are case-sensitive
variable is defined and set initial value in Template or Template Stack, initial value can be override in template stack, to setup individual value for each FW stack, Export and Import Variable CSV.
On firewall, panorama pushed settings shows Read-Only, but can be override.
Device Group : Policies, Objects - FW belongs to a single device group
Global shared group contains device group
Device groups are in hierarchy, children group inherits settings from parent; Templates are independent settings, Template Stack combines them together, and resolve conflict by templates order.
By default, Panorama will use the value in the lowest group in the hierarchy
When you make changes to a firewall in an HA pair, Panorama sends the appropriate changes to each firewall separately. This operation is different from how redundant firewall pairs operate without Panorama.
You might have an item that you do not want modified for any reason in any descendant device groups. If you check the box for Disable override on the element itself
This behavior is different from the behavior in templates. You can modify an element directly on a managed firewall when that element has been pushed down through a template from Panorama. You cannot modify an object directly on a managed firewall when that object has been pushed down through a device group from Panorama.
Policies
Post Rules
Default Rules
Deploy order: Local rule takes precedence, but can be change to Shared group take precedency.
shared group
device group
local config
no local device edit of shared object and policy
shared pre policy
device group pre policy
local FW policy
device group post policy
shared post policy
combined rules preview.
yellowdot =override
Context - switch between global to individual device
commit - Panorama|
push - device
Troubleshooting
1. on Panorama:
show devices all
2. on firewall:
show panorama-status
========
Server error : Failed to change system mode from management-only to panorama.
Please add a new virtual logging disk with more than 50.00 GB of storage capacity to support panorama mode.
Not enough RAM: Found 7.78 GB, need 16.0 GB to support panorama mode.
Not enough CPU cores: Found 4 cores, need 8 cores to support panorama mode
Resource List
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PMjGCAW




Comments
Post a Comment