Situation:
Attacker attempts to connect Anyconnect, Anyconnect sends authentication to ISE, ISE sends authentication to AD. In ISE logs, there are lots failed Radius requests with non-exist username, AD is overwhelmed, can't process more legitimate AD authentication request. During this attack, ISE normally is not the one get overwhelmed.
Anyconnect user's public IP is in Radius attribute calling-station-ID
Issue:
Cisco Enhancement request:
Anyconnect authentication failure syslog message
After change syslog severity:
ASA(config)#logging message 113015 level warnings
Feb 04 2025 20:40:30: %ASA-4-113015: AAA user authentication Rejected : reason = Invalid password : local database : user = tom: user IP = 192.168.2.151
Solution:
Appendix 1
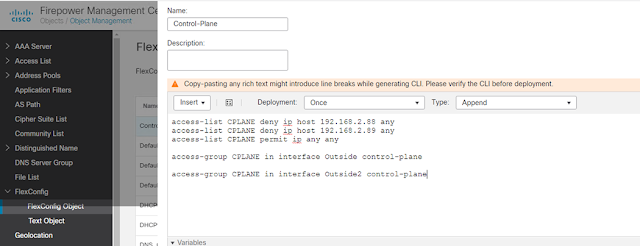
1. 1. Add FlexConfig Object as below, replace with real IP and interface name.
2. 2. Configure FlexConfig Poilcy, apply the FlexConfig Object
3. 3. Deploy policy
Appendix 2
New Cisco ASA and FTD features block VPN brute-force password attacks
ASA:
Implement Hardening Measures for Secure Client AnyConnect VPN
https://www.cisco.com/c/en/us/support/docs/security/secure-client/221880-implement-hardening-measures-for-secure.htmlThese threat detection features are currently supported in the Cisco Secure Firewall versions listed next:
ASA Software:
- 9.16 version train -> supported from 9.16(4)67 and newer versions within this specific train.
- 9.17 version train -> supported from 9.17(1)45 and newer versions within this specific train.
- 9.18 version train -> supported from 9.18(4)40 and newer versions within this specific train.
- 9.19 version train -> supported from 9.19(1).37 and newer versions within this specific train.
- 9.20 version train -> supported from 9.20(3) and newer versions within this specific train.
- 9.22 version train -> supported from 9.22(1.1) and any newer versions.
FTD Software:
- 7.0 version train -> supported from 7.0.6.3 and newer versions within this specific train.
- 7.2 version train -> supported from 7.2.9 and newer version within this specific train.
- 7.4 version train -> supported from 7.4.2.1 and newer version within this specific train.
- 7.6 version train -> supported from 7.6.0 and any newer versions.



Comments
Post a Comment