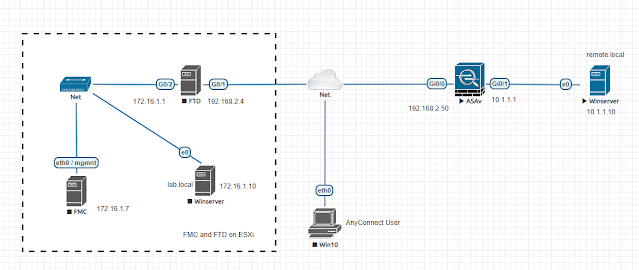
Scenario:
Anyconnect user connects to FTD authenticate to remote AD remote.local via S2S VPN tunnel.
Issue:
Assume S2S between FTD and ASAv (172.16.1.0/24 <=>10.1.1.0/24) is fully configured and operational.
FTD LDAP configuration has no interface, whereas ASA has.
aaa-server RemoteAD host 10.1.1.10
server-port 389
ldap-base-dn dc=corp,dc=local
ldap-group-base-dn dc=corp,dc=local
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn ldap@corp.local
server-type microsoft
ldap-attribute-map RemoteAD
FTD67#
Without configuring LDAP query interface in FTD, query using routing table to determine egress interface, this this case, query is sourced
from Outside interface. When FTD S2S VPN has Route Injection for 10.1.1.0/24, the LDAP query to 10.1.1.10 on FTD goes nowhere.
Packets are captured on FTD outside, inside or ASP-drop don't show ldap query.
When FTD S2S VPN doesn't have Route Injection for 10.1.1.0/24, ldap query is sent to FTD outside interface shows as
192.168.2.4 > 10.1.1.10 389
Solution1 summary:
Add the ldap query to FTD S2S tunnel ACL:
permit tcp host 192.168.2.4 host 10.1.1.10 eq ldap
on ASA:
access-list VPN-ACL extended permit tcp host 10.1.1.10 eq ldap host 192.168.2.4
nat (inside,outside) source static host-10.1.1.10 host-10.1.1.10 destination static FW-192.168.2.4 FW-192.168.2.4 no-proxy-arp route-lookup
Configuration Notes
The configuration is to use LDAP Attribute map to check if the user belongs to Remote AD group ACUsers.
LDAP Attribute Value is case sensitive. If doesn't match the value exactly, no group policy is mapped, debug ldap will display if the mapping works.
CN=ACUsers,CN=Users,DC=corp,DC=local
When mapping works, debug has
[37] memberOf: value = CN=ACUsers,CN=Users,DC=corp,DC=local
[37] mapped to Group-Policy: value = GP-Anyconnect
[37] mapped to LDAP-Class: value = GP-Anyconnect
Solution 2 summery.
Proxy authentication to remote AD, example is using internal ISE
Option1:
join ISE to Active Directory, configure FTD to use ISE as radius sever.
Note: configure local DNS server Conditional Forwarder is required to locate corp.local. Ignore Server FQDN is unable to resolve error.
Option 2:
Configure LDAP on ISE, so FTD to ISE is Radius, ISE to AD is LDAP.
By default, when an user connects, username should use UPN form: acuser@corp.local.
Using username "acuser" will get authentication failed and INVALID username logged in ISE. This is because ISE uses UPN name to search LDAP by default, to change it to use sAMAccountName, do following:
ISE > External Identity Source > LDAP > "LAB-LDAP" > General > Schema, change it to Custom, then change it back to Active Directory, change Subject Name Attribute from UserPrincipalName to sAMAccountName.











Comments
Post a Comment