Solution 1 - local-in-policy
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Restricting-Allowing-access-to-the-FortiGate-SSL/ta-p/222845
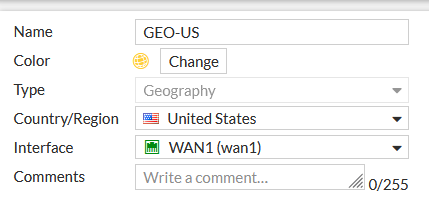
1. Create geography objects for US, Canada and RFC1918 IP addresses.
2. Add local-in-policy
config firewall local-in-policy
edit 1
set intf "wan1"
set srcaddr "G - ALL PRIVATE ADDRESS RANGES" "GEO-Canada" "GEO-US"
set dstaddr "WAN1-192.168.2.33"
set action accept
set service "HTTPS"
set schedule "always"
next
edit 2
set intf "wan1"
set srcaddr "all"
set dstaddr "WAN1-192.168.2.33"
set service "HTTPS"
set schedule "always"
next
end
Solution 2 - source-address-negate
https://community.fortinet.com/t5/FortiGate/Technical-Tip-How-to-block-SSL-VPN-Connection-from-a-certain/ta-p/206883
1. Create an address and address group
2. CLI
FortiGate-70F (settings) # set source-address Block_SSLVPN_Group
FortiGate-70F (settings) # set source-address-negate enable
3. Verification
No log found



Comments
Post a Comment