Manual Enrollment.
1. FMC > Objects > PKI >Cert Enrollment
1.1 Manual Enrollment, CA Certificate can leave blank temporally, but once Device Certificate is added at next step, CA Certificate will be grey out.
Include the custom FQDN, otherwise, browser may still give error even CN and SAN look good. "ERR_CERT_COMMON_NAME_INVALID"
CN will be automatically Added to SAN in the CA issued certificate. 2. Devices > Certificates, "Add"
click "ID" button to generate CSR
Once get the certificate, import above.
If CA info is blank in step 1, we will see:
Note FMC PKI Trusted CAs is not used for FTD device certificate, so import CA there doesn't resolve the issue.
We need delete the device certificate in order to add the missing CA info in the enrollment, then add the device certificate again, Click ID button to display CSR (this is always the same one, doesn't need be re-sent to CA.) and import the certificate.
3. To renew a manual enrolled certificate, click "Re-enroll certificate" button to display the CSR. For PKCS12 enrolled cert, re-enroll button will re-import the file.
1. FMC > PKI > Cert Enrollment
Import the existing PKCS12 file, in this case, the key pair may generated somewhere else
Note:
For PFX file exported from ASA ASDM, after manual import into FMC, it may get the following CA error, this is because the PFX file doesn't include the CA certificate, import CA certificate to FMC>Objects>PKI won't help. The PCKS12 file need be bind CA certificate before imported, refer Appendix to resolve this error.
2. To create a new PCKS file, first generate the key pair somewhere, like FMC or FTD.
openssl req -new -newkey rsa:2048 -nodes -keyout private.key -out ftd1.csr
input certificate parameters.ca ftd1.csrCopy the generated CSR and send it to a CA, when get new cert, load it to FMC or FTD via SCP or create the cert file 2.1 admin@FTD67:~$ scp admin@172.16.1.10:ftdvpn.cer ftdvpn.cer
2.2 use vi
vi ftdvpn.cer
i
Shift+Insert (open received cert in notepad, paste in vi)
:wq!
bind cert, private key and ca certificate into a PKCS12 file.openssl pkcs12 -export -out ftd.pfx -in ftd.crt -inkey private.key -certfile ca.crt
If the certificate is a part of a chain with a root CA and 1 or more intermediate CAsopenssl pkcs12 -export -out ftd.pfx -in ftd.crt -inkey private.key -chain -CAfile cachain.pem
If a PKCS7 file (.p7b, .p7c) is returned, these commands can also be used to create the PKCS12. If the p7b is in der format, ensure to add -inform der to the arguments, otherwise do not include it:
openssl pkcs7 -in ftd.p7b -inform der -print_certs -out ftdpem.crt openssl pkcs12 -export -in ftdpem.crt -inkey private.key -out ftd.pfx
3. Once pkcs file is generated on FTD, instead of using third party SCP tool, do this:
cp ftd.pfx /ngfw/var/common
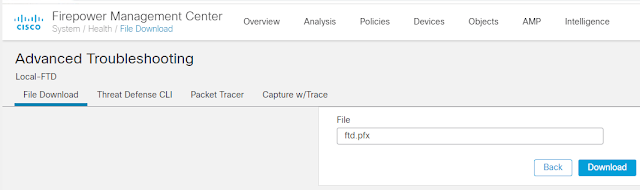
go to FMC device Advanced Troubleshooting, download the pkcs12 file as below.
Appendix --- Resolve the issue related to the pfx file export from ASDM.
The pfx file vpn.pfx has extra blank line at the top, extract cert will get failure as below.
root@FTD67:/home/scpuser# openssl pkcs12 -in vpn.pfx -nokeys -out certs.pem
139674416155392:error:0D0680A8:asn1 encoding routines:ASN1_CHECK_TLEN:wrong tag:tasn_dec.c:1220:
139674416155392:error:0D07803A:asn1 encoding routines:ASN1_ITEM_EX_D2I:nested asn1 error:tasn_dec.c:386:Type=PKCS12
root@FTD67
Solution:
use vi open vpn.pfx
move the cursor to the top, use "dd" to delete that line
:wq!
:wq!
root@FTD67:/home/scpuser# openssl pkcs12 -in vpn.pfx -nokeys -out cert.pem
Enter Import Password:
MAC verified OK
root@FTD67:/home/scpuser# openssl pkcs12 -in vpn.pfx -nocerts -out key.pem
Enter Import Password:
MAC verified OK
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
Bind intermediate cert and root cert into on file ca.pem
openssl pkcs12 -export -out newvpn.pfx -in cert.pem -inkey key.pem -chain -CAfile ca.pem
root@FTD67:/home/scpuser# openssl pkcs12 -export -out newvpn.pfx -in certs.pem -inkey key.pem -chain -CAfile ca.pem
Enter pass phrase for key.pem:
Enter Export Password:
Verifying - Enter Export Password:
Resolve the issue related to the pfx file export from CLI or FMC
the pfx export from ASA CLI or FMC is base64 format, needs convert to binary format before use openssl to retrieve cert or key.
openssl enc -base64 -d -in vpn.pfx -out vpnnew.pfx
============
In FMC 6.4 and above, SCP to the FMC is not possible directly. For that, the following is needed(the below is intended for user: admin):
root@FMC:/Volume/home/admin# usermod --shell /bin/bash admin
After this SCP to the FMC will work. Once done, please remeber to rollback:
root@FMC:/Volume/home/admin# usermod --shell /usr/bin/clish admin
list existing users:
less /etc/passwd
root@FTD67:/home/admin# useradd scpuser
root@FTD67:/home/admin# passwd scpuser
New password:
Retype new password:
passwd: password updated successfully
root@FTD67:
===============
https://www.cisco.com/c/en/us/support/docs/security-vpn/public-key-infrastructure-pki/215850-certificate-installation-and-renewal-on.html









Comments
Post a Comment