=======Active Authentication==========
Firewall actively authenticate an user before allow the access. This is done by two methods:
1. Active authentication enabled on firewall policy
Add user or user group to Source
2. Active authentication enabled on interface via Captive portal
1. local user and group
2. remote user and group
- remote user: Create a remote user type (RADIUS/TACAS+/LDAP), specify remote server then select an user account.
- remote user group: Create a Firewall type user group, then map it to a remote group.
3. MFA
two free tokens
User & Authentication > Fortitoken
For administrator, assign a token to an administrator, an email with barcode will be sent out, open Fortitoken mobile app, scan the barcode.
User group Types:
- Firewall
- Guest - wireless guest
- FSSO - AD/LDAP
- RSSO - Radius
Protocol trigger active authentication: http/https/ftp/telnet
Active authentication is intended to be used as a backup when passive authentication fails.
========Passive Authentication==========
1. FSSO and DC agent
This is used to get user/IP mapping from AD, so FW knows which user owns a session.
- Domain Controller (DC) agent
- Citrix/Terminal Server (TS) agent
- Collector agent (CA)
FSSO mode:
# DC mode: DC Agent is installed on each domain controllers, at least one Collector agent (CA) is installed on a domain member server. DC Agent sends info to CA, CA sends info to Fortigate.
# Polling mode: One CA is installed on one domain member server, it polls info from DC without agent installed on DC..
In polling mode there are three options: NetAPI polling, Event log polling, and Event log using WMI.
# Agentless: Fortigate collects data directly from domain controller, event Log Polling is used. Less some features.
DC agent mode is the standard mode for FSSO.
2. FSSO Configuration
2.1 Agentless Polling Mode
Security Fabric > External Connectors > Poll Active Directory Server, specify LDAP server info.
2.2 Collector agent-based polling or DC Agent Mode
Security Fabric > External Connectors > FSSO Agent on Windows AD
diag debug enable
diag debug authd fsso server-status
diag debug authd fsso list
3. FSSO TS
diag debug authd fsso ....
diag debug authd fsso-polling ....
4. Create FSSO type user group, then use the group in Firewall Policy
===================
LDAP
This used to pull AD group from AD, then these AD groups can be used in security policy or firewall admin access.
Type of User Group
1. Firewall - can be local group or remote group.
2. Guest
3. FSSO - Fortinet single sing-on
4. RSSO - Radius single sing-on
----------------------
Use AD account for Firewall access:
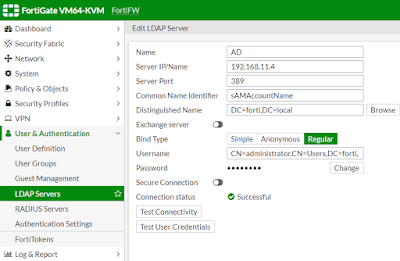
1. Create LDAP server
or:
#diag test autheserver ldap <server_name> <username> <password>
2. Create User Groups by retrieving AD groups from LDAP server
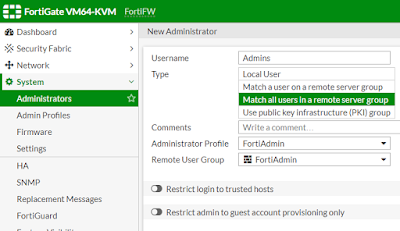
3. Create Admin Profile which defines permissions.
4. Create an Administrator account, associate with an Admin Profile and User Group.
--------------------------
Use AD account for Internet access:
2. Method 1: Edit firewall policy to include both IP and User Group in source
if there is another policy below allows NET-10.0.1.0/24 access Internet, there will be no authentication prompt. This behaviors can be changed by enforce authentication on demand (CLI only)
#config user setting
(setting) # set auth-on-demand Always.
3. Method 2: Enable Captive Portal on inside interface
4.User access Internet get prompt
Authentication timeout
default is 5 minutes
#config user setting
set auth-timeout xx
Monitor Users
Dashboard > User & Devices > Firewall Users
diag firewall auth list (clear)
Captive Portal Excemption
1. # config user security-example-list
2. # config firewall policy
edit <policy_id>
set captive-portal-example enable.







Comments
Post a Comment