Virtual systems are supported on PAN-OS 11.1.3 and later releases VM-Series firewalls,PA-400 Series (PA-440, PA-445, PA-450, PA-455, and PA-460 only), PA-1400 Series, PA-3200 Series, PA-3400 Series, PA-5200 Series, PA-5400 Series, and PA-7000 Series firewalls.
Virtual Systems license is required
To activate vSYS, VM needs FLEX-VM license and 16 vCPU
1. Request Software NGFW Credit evaluation.
2. When receive Activation email, click "Active" in the email.
3. Follow the link, add the credit to correct PA support account.
4. Create deployment profile, set FW VM number, vCPU number, vSYS number etc...
5. Deploy a new PA VM with 24G RAM and 16 vCPU (Tier 3), complete basic configure so management interface can reach Internet
6. In CSP credit page, client "detail" button
6. Click the three dot at far right, click "Register Firewall", copy the "Authorization Code"
7. In PA VM license page, click "Activate features using Authorization Code"
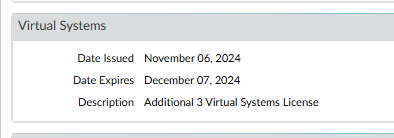
8. After system reload, verify vSYS license
9. Enable vSYS in setup.
If VM doesn't have Tire3 or required CPU/RAM, will get the following error
Configuration
1. Create vsys
ID
name
2. Create zones
assign zone to a vsys
3. Configure interface
Scenario 1: shared default VR "default"
a. add static route
vsys A can't talk to vsys B even they are using the same default VR.
To allow vsys A talk to vsys B
1. configure the vsys visible to each other
2. Create External zone for each vsys, add available visible vsys
all External zones trust each other
3. Create security rules
vsys-A trust > vsys-A External
vsys-B External > vsys-B trust or untrust
Scenario 2: Dedicated VR for each vsys.
1. configure zone visibility and external zone
2. To reach subnet in another VR, use "Next VR" as Next Hop.
Scenario 2: Shared Gateway
2. Create a new virtual router VR_SG1, add static routes
3. Edit other vsys, point default route to next VR SG1
4. Create a new zone for SG, assign interface
5. Create NAT in SG1 shared gateway
remove NAT in other vsys
SG1 policies only have NAT and PBR
For other system to use SG, they need firewall policy to allow destination to their External zone, then be routed to SG





















Comments
Post a Comment