Summary
1. Checkpoint GW configuration for S2S VPN
2. Add Interoperable Device for ASA
3. Add VPN Community
4. Add Policy rules.
======================
1. Checkpoint GW configuration for S2S VPN
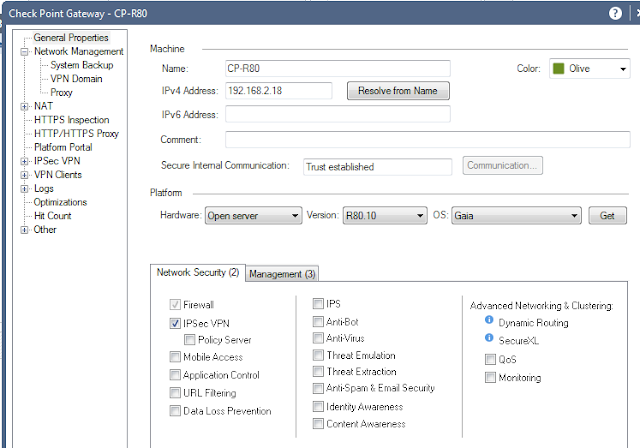
1.1 "IPSec VPN" blade is selected.
1.2 Verify network topology
1.3 Network Management > VPN Domain
Or set Specific VPN domain for Gateway Communities (R80.40)
2. Add Interoperable Device for ASA
2.1 Specify remote peer IP address
2.2 Topology>VPN Domain
3. Add VPN Community
3.1 Create a Meshed Community, add local and remote gateways to the list
3.2 Configure Phase I and Phase II parameters
3.3 Tunnel Management, select per subnet pair
3.4 Configure Shared Secret
3.5 Advanced section to set life time and disable NAT inside the VPN community
4. Verify VPN ip address
by default, main address is selected, which is the IP in "General Properties" section.
5. Add rule
6. Note
in case local IP is NATed before go to VPN tunnel
- Create NAT rule
- VPN domain includes both real IP and NATed IP
- Access Rule use original IP
========= Routed base VPN=======
If you configure a Security Gateway for Domain Based VPN and Route Based VPN, Domain Based VPN takes precedence by default.
To force Route Based VPN to take priority, you must create a dummy (empty) group and assign it to the VPN domain
Summary Steps
3. Create VPN Community
peer name will be used in VTI creation.
Set Tunnel Management to "One VPN tunnel per Gateway pair"
4. Create an empty group, point local VPN domain to the empty group
5. Login Gaia, add a VPN tunnel interface.
Remote peer name is defined in the VPN community.You must define the two peers in the VPN community before you can define the VTI.
can be numbered or unumbered
6 Add Access rules
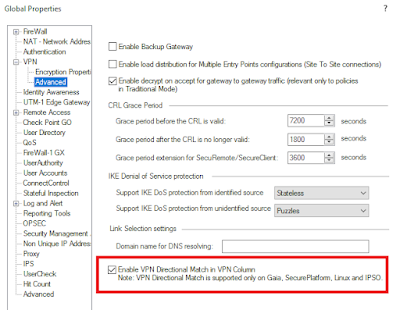
Directional matching is necessary for Route Based VPN when a VPN community is included in the VPN column in the rule. This is because without bi-directional matching, the rule only applies to connections between a community and an encryption domain (Domain Based Routing).
The directional rule must contain these directional matching conditions:
Community > CommunityCommunity > Internal_ClearInternal_Clear > Community
is the name of a VPN Community.
refers to all traffic from IP addresses to and from the specified VPN community.
Note - It is not necessary to define bidirectional matching rules if the VPN column contains the value.
Verification:
1. TS will be all "0"
2. VTI has increasing packets.
SG> show interface vpnt1
state on
mac-addr Not configured
type vpnt
link-state not available
mtu 1500
auto-negotiation Not configured
speed N/A
ipv6-autoconfig Not configured
duplex N/A
monitor-mode Not configured
link-speed Not configured
comments
vpn-tunnel-id 1
vpn-peer ASAv
vpn-physical-device eth0
ipv4-address Not Configured
ipv6-address Not Configured
ipv6-local-link-address Not Configured
Statistics:
TX bytes:88032 packets:1048 errors:0 dropped:0 overruns:0 carrier:0
RX bytes:3967824 packets:47236 errors:0 dropped:0 overruns:0 frame:0
SG>
===============Troubleshooting========
1. vpn tu
only view SAs
CP-R80> vpn tu
********** Select Option **********
(1) List all IKE SAs
(2) * List all IPsec SAs
(3) List all IKE SAs for a given peer (GW) or user (Client)
(4) * List all IPsec SAs for a given peer (GW) or user (Client)
(5) Delete all IPsec SAs for a given peer (GW)
(6) Delete all IPsec SAs for a given User (Client)
(7) Delete all IPsec+IKE SAs for a given peer (GW)
(8) Delete all IPsec+IKE SAs for a given User (Client)
(9) Delete all IPsec SAs for ALL peers and users
(0) Delete all IPsec+IKE SAs for ALL peers and users
* To list data for a specific CoreXL instance, append "-i <instance number>" to your selection.
(Q) Quit
*******************************************
==============
Proxy-ID related issue:
1. ASA is policy-based VPN, Checkpoint is "One VPN tunnel per subnet pair".
This is recommended configuration.
2. ASA is policy-based VPN, Checkpoint is "One VPN tunnel per Gateway pair".
Traffic initiates from ASA side can bring up the tunnel quickly, but if the traffic initiate from Checkpoint side, it may take one or two minutes even more to bring up the tunnel.
3. ASA is policy-based VPN, Checkpoint is "One VPN tunnel per host pair".
tunnel comes up with host Proxy-ID
==========
| How to configure IPsec VPN tunnel between Check Point Security Gateway and Amazon Web Services VPC using static routes |
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk100726
How to set up a Site-to-Site VPN with a 3rd-party remote gateway
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk53980
Route Based VPN
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_SitetoSiteVPN_AdminGuide/Topics-VPNSG/Route-Based-VPN.htm
Simplified-Mode vs. Traditional-Mode VPNs
| Commands | Descriptions |
|---|
| vpn tu | VPN utility, allows you to rekey vpn |
| vpn ipafile_check ipassignment.conf detail | Verifies the ipassignment.conf file |
| dtps lic | show desktop policy license status |
| cpstat -f all polsrv | show status of the dtps |
| vpn shell | Start the VPN shell |
| vpn shell /tunnels/delete/IKE/peer/[peer ip] | delete IKE SA |
| vpn shell /tunnels/delete/IPsec/peer/[peer ip] | delete Phase 2 SA |
| vpn shell /show/tunnels/ike/peer/[peer ip] | show IKE SA |
| vpn shell /show/tunnels/ipsec/peer/[peer ip] | show Phase 2 SA |
| vpn shell show interface detailed [VTI name] | show VTI detail |
| vpn debug ikeon|ikeoff | Debug IKE into $FWDIR/log/ike.elg. Analyze ike.elg with the IKEView tool |
| vpn debug on|off | Debug VPN into $FWDIR/log/vpnd.elg. Analyze vpnd.elg with the IKEView tool |
| vpn debug trunc | Truncate and stamp logs, enable IKE & VPN debug |
| vpn drv stat | Show status of VPN-1 kernel module |
| vpn overlap_encdom | Show, if any, overlapping VPN domains |
| vpn macutil <user> | Show MAC for Secure Remote user <user> |
| vpn ver [-k] | Check VPN-1 major and minor version as well as build number and latest hotfix. Use -k for kernal version
|

















PureVPN is offering 88% off on early black Friday at just $1.33 per month with multiple features such as 6500+ servers in more than 98 locations, split tunnelling, internet kill switch, no-log privacy, 10 multi logins, 24/7 customer support and much more.
ReplyDelete