https://community.cisco.com/t5/security-knowledge-base/how-to-integrate-meraki-networks-with-ise/ta-p/3618650
VLAN1 Management 172.16.10.0/24
VLAN10 Guest 192.168.10.0/24
VLAN11 Workstation 172.16.11.0/24
VLAN12 MAB 172.16.12.0/24
VLAN10 Guest 192.168.10.0/24
VLAN11 Workstation 172.16.11.0/24
VLAN12 MAB 172.16.12.0/24
Wireless 802.1x
Meraki Configuration
Group Policy:
Employee:
Contractor: L3 FW rules Deny Youtube and Facebook
SSID: corp
Security: my RADIUS server
Splash: Cisco Identity Services Engine (ISE) Authentication.
RADIUS attribute specifying group policy name: Airespace-ACL-Name
Client IP: Bridge
VLAN tagging: VLAN 11
ISE Configuration:
Create device group type: Meraki Wireless, add Meraki AP to the group.
Policy Set: Condition matches Meraki Wireless device group type
Authorization Profiles:
MerakiWirelessEmployee:
Airespace ACL Name: Employee
MerakiWirelessContractor:
Airespace ACL Name: Contractor
Authentication Policy:
Condition: Wireless_802.1x
Use: AD
Authorization Policy:
Condition: Wireless_802.1x & match AD group Employees or Contractors.
Result: Authorization Profiles MerakiWirelessEmployee or MerakiWirelessContractor
Verification:
Meraki client has proper Group Policy applied
Wireless MAB
Meraki Configuration
Group Policy: Workstation
Security: MAC-based access control (no encryption)
Splash: Cisco Identity Services Engine (ISE) Authentication
RADIUS attribute specifying group policy name: Airespace-ACL-Name
Client IP: Bridge
VLAN tagging: VLAN 12
ISE Configuration:
Create device group type: Meraki Wireless, add Meraki AP to the group.
Policy Set: Condition matches Meraki Wireless device group type
Authorization Profiles:
MerakiWirelessWorkstation:
Airespace ACL Name: Workstation
Authentication Policy:
Condition: Wireless_MAB, Under Options: If user not found, select Continue
Use: Internal Endpoints
Authorization Policy:
Condition: Wireless_MAB
Result: Authorization Profiles MerakiWirelessworkstation
https://documentation.meraki.com/MS/Access_Control/Meraki_MS_Group_Policy_Access_Control_Lists
Wireless 802.1x
Meraki Configuration
Group Policy:Employee:
Contractor: L3 FW rules Deny Youtube and Facebook
SSID: corp
Security: my RADIUS server
Splash: Cisco Identity Services Engine (ISE) Authentication.
RADIUS attribute specifying group policy name: Airespace-ACL-Name
Client IP: Bridge
VLAN tagging: VLAN 11
ISE Configuration:
Create device group type: Meraki Wireless, add Meraki AP to the group.Policy Set: Condition matches Meraki Wireless device group type
Authorization Profiles:
MerakiWirelessEmployee:
Airespace ACL Name: Employee
MerakiWirelessContractor:
Airespace ACL Name: Contractor
Authentication Policy:
Condition: Wireless_802.1x
Use: AD
Authorization Policy:
Condition: Wireless_802.1x & match AD group Employees or Contractors.
Result: Authorization Profiles MerakiWirelessEmployee or MerakiWirelessContractor
Verification:
Meraki client has proper Group Policy applied
Wireless MAB
Meraki Configuration
Group Policy: WorkstationSecurity: MAC-based access control (no encryption)
Splash: Cisco Identity Services Engine (ISE) Authentication
RADIUS attribute specifying group policy name: Airespace-ACL-Name
Client IP: Bridge
VLAN tagging: VLAN 12
ISE Configuration:
Create device group type: Meraki Wireless, add Meraki AP to the group.Policy Set: Condition matches Meraki Wireless device group type
Authorization Profiles:
MerakiWirelessWorkstation:
Airespace ACL Name: Workstation
Authentication Policy:
Condition: Wireless_MAB, Under Options: If user not found, select Continue
Use: Internal Endpoints
Authorization Policy:
Condition: Wireless_MAB
Result: Authorization Profiles MerakiWirelessworkstation
Wired 802.1x (MAB)
Meraki Configuraiton:
Access-policy: ISE-HYBRID
Radius server: ISE
Accounting enabled, CoA enabled
RADIUS attribute specifying group policy name: Filter-ID
Host mode:
Access policy type: Hybrid authentication
Optional Guest VLAN 10
Assign Access Policy to a switch port.
ISE Configuration
Create device group type: Meraki Switches, add Meraki switches to the group.
Policy Set: Condition matches Meraki Switches device group type
Authentication Policy:
Wired Dot1X:
condiction: Wired_802.1x
use: AD
Wired MAB:
condition:Wired_MAB
use: Internal Endpoints
Authorization Policy:
Domain PC Dot1x:
Condition:Wired_802.1x & AD group Domain Computer
Result: MerakiWiredDomainPC, contains Filter-ID to match Group Policy on Meraki
Employee Dot1X:
Condition:Wired_802.1x & AD group Employees
Result: MerakiWiredEmployee, contains Filter-ID to match Group Policy on Meraki
Wired Guest: --for non-employee PC with 802.1x enabed. For example, contractor
Condition:Wired_802.1x
Result: MerakiWiredGuest, which assign guest VLAN 10
Wired 802.1x (MAB)
Meraki Configuraiton:
Access-policy: ISE-HYBRIDRadius server: ISE
Accounting enabled, CoA enabled
RADIUS attribute specifying group policy name: Filter-ID
Host mode:
Access policy type: Hybrid authentication
Optional Guest VLAN 10
Assign Access Policy to a switch port.
ISE Configuration
Create device group type: Meraki Switches, add Meraki switches to the group.Policy Set: Condition matches Meraki Switches device group type
Authentication Policy:
Wired Dot1X:
condiction: Wired_802.1x
use: AD
Wired MAB:
condition:Wired_MAB
use: Internal Endpoints
Authorization Policy:
Domain PC Dot1x:
Condition:Wired_802.1x & AD group Domain Computer
Result: MerakiWiredDomainPC, contains Filter-ID to match Group Policy on Meraki
Employee Dot1X:
Condition:Wired_802.1x & AD group Employees
Result: MerakiWiredEmployee, contains Filter-ID to match Group Policy on Meraki
Wired Guest: --for non-employee PC with 802.1x enabed. For example, contractor
Condition:Wired_802.1x
Result: MerakiWiredGuest, which assign guest VLAN 10
Wireless LWA Guest
Local Web Authentication - LWA: Meraki cloud serves the login page, then send Radius request to ISE for AAA.
Meraki Configuraiton:
Splash: Sign-on with my RADIUS server
RADIUS for splash page, enter the publicly reachable IP address.
Radius request is from Meraki cloud,, not from local Meraki devices, Meraki cloud IPs can be found from Help > Firewall info
209.206.48.0/20209.206.48.0/20, 216.157.128.0/20, 158.115.128.0/19
209.206.48.0/20209.206.48.0/20, 216.157.128.0/20, 158.115.128.0/19
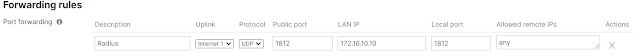
MX should have port forwarding, no Inbound L3 rule is required.
the Test button in Radius configuration section won't work, it doesn't generate Radius request from Meraki could.
ISE Configuration
For this type of Guest WiFi, ISE receives the Service-Type is Login
- Authentication Policy:
use ISE local user account in this lab
use ISE local user account in this lab
- Authorization Policy
Simple PermitAccess, no additional Attribute.
Simple PermitAccess, no additional Attribute.
Wireless MAB Guest
Meraki Configuration
Group Policy: Guest
Security: MAC-based access control (no encryption)
Splash: Cisco Identity Services Engine (ISE) Authentication
RADIUS attribute specifying group policy name: Airespace-ACL-Name
Client IP: Bridge
VLAN tagging: VLAN 10
ISE Configuration:
- Policy Set
- Authorization Profiles:
2. Self Registration Profile
3. Sponsored Profile
MerakiWirelessWorkstation:
Airespace ACL Name: Guest
4. Wireless Guest Profile
- Authentication Policy:
Under Options: If user not found, select Continue
- Authorization Policy:
Only one of portal policies should be enabled, client first connects to the portal, then new radius request will hit "Guest Access" rule
Client VPN:
209.206.48.0/20209.206.48.0/20, 216.157.128.0/20, 158.115.128.0/19, Your network(s)










Comments
Post a Comment