Configure FMC with LDAP for External Authentication
1. System > Users > External Authentication, Add External Authentication Object
Set Defaults button will automatically fill up Attribute Mapping section.
Once configures host info, Fetch DNs can retrieve Base DN
NetworkAdmins is AD group, only members in this AD group can login FMC/FTD. In this lab, maps it to FMC Administrator group, don't select any Default User Role, once you select one, you can't unselect it.
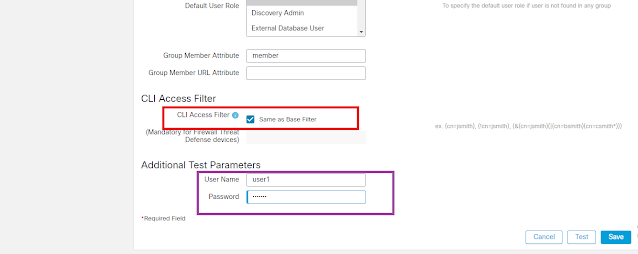
CLI Access Filter:
when check "Same as Base Filter", cli access doesn't check user's AD group info, so all AD user will get access FMC/FTD cli.
To restrict cli access, we can add a new AD attribute, in this lab, it is called "firepowercli". Refer this article to create a Unicode String attribute, restart AD Domain Services, then in AD set the value to "shell" for user needs FMC/FTD cli access.
https://www.rebeladmin.com/2017/11/step-step-guide-create-custom-active-directory-attributes/
Then configure :
Test will show how many users has shell access and which user has.
Test button also reports which FMC admin group is assigned
user is assigned to FMC Administrator group
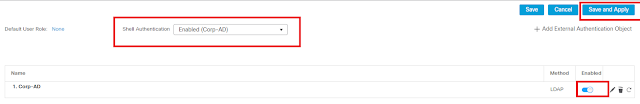
2. Leave Default role to None, enabled AD for Shell Authentication, Enable the LDAP object Corp-AD, Save and Apply
- When an AD user exists and in the specified AD group (which maps to Administrator role ), user will be automatically created in FMC user list, with Role Administrator and External Authentication Method.
- When an AD user exists, password is correct but group mapping is wrong, user get:
- When the admin user exist but password is wrong, no local user is created on FMC
Configure FTD with LDAP for External Authentication
https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/215538-configure-firepower-management-center-an.html#toc-hId-1407814223
FTD SSH and HTPPs access
commands to restrict access from specified IPs
configure https-access-list (local manager only)
configure ssh-access-list
The ssh access list was changed successfully.
>
> show ssh-access-list
ACCEPT tcp -- 192.168.2.0/24 anywhere state NEW tcp dpt:ssh
>
By default, FTD SSH is only enabled on MGMT interface, to enable it on data interface, need configure platform setting:
HTTPS access is specifically useful to download the packet captures from the diagnostic secure web interface directly for the analysis.
But it gives Authorization Required message, couldn't download capture via https
We can download CLI capture via copy command, must be in LINA CLI:
copy /pcap capture:CP ftp://ftpusername@192.168.2.111/ftp/CP.pcap
Configure FMC and FTD External Authentication with ISE as a RADIUS Server
ISE Configuration
Two Authorization Profiles
Class can be added from Advanced Attribute Setting> Radius > Class, set class value, or choose Common Tasks > ASA VPN, set class value
https://www.cisco.com/c/en/us/support/docs/security-vpn/remote-authentication-dial-user-service-radius/221009-configure-fmc-and-ftd-external-authentic.html
FTD CLI Access with RADIUS
1. Use the existing External Authentication ISE inn platform setting.
ISE policy:
In FTD expert mode, same AD password for sudo.
https://bluenetsec.com/ftd-cli-access-with-radius/
**********
CSCwb62059
Unable to login to FTD using external authentication
CSCwe72535


















Comments
Post a Comment