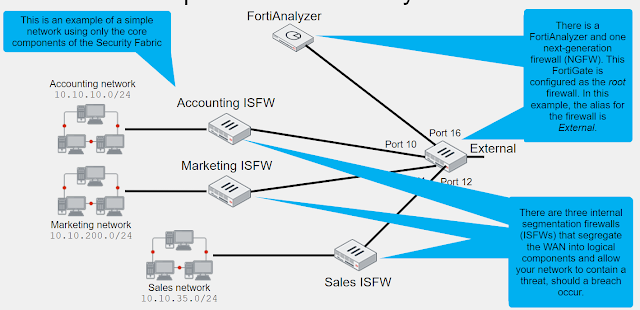
Core:
- Minimum of two Fortigate devices: one root, and one or more downstream
- At least one of: FortiAnalyzer, FortiAnalyzer Cloud, or FortiGate Cloud
LAB notes:
on FGT, add FAZ got error, from cli:
exec log fortianalyzer test-connectivity
Failed to get FAZ's status. SSL error. (-3)
Solution:
on FAZ:
FAZVM64 # config system global
(global)# set enc-algorithm low
(global)# set ssl-low-encryption enable
(global)# set oftp-ssl-protocol tlsv1.0
(global)# end
enc-algorithm setting change will cause all existing FGFM tunnel/WebService connection reset. Do you want to continue? (y/n)y
Local-Fortigate # show system csf
config system csf
set status enable
set group-name "fortinet"
config trusted-list
edit "xxxxx"
set serial "xxxxx"
set index 1
next
end
end
Local-Fortigate # show full system csf
config system csf
.....
set downstream-access disable
!!Enable/disable downstream device access to this device's configuration and data.
set configuration-sync default
!! default Synchronize configuration for IPAM, FortiAnalyzer, FortiSandbox, and Central Management to root node.
!! local Do not synchronize configuration with root node
set fabric-object-unification default
!!on root only
!!default Global CMDB objects will be synchronized in Security Fabric.
!!local Global CMDB objects will not be synchronized to and from this device.
.....
end

Comments
Post a Comment