Notes:
> !!operation mode
# !!configuration mode
serial cable
wait for prompt "PA-VM" then login with below default account.
admin/admin
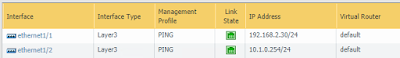
HW FW management port default IP is 192.168.1.1,
VM FW management port doesn't have a static IP, it is DHCP client.
show interface management
To change mgmt IP:
configure
set deviceconfig system type static
set deviceconfig system ip-address 172.16.1.100
set deviceconfig system netmask 255.255.255.0
set deviceconfig system default-gateway 172.16.1.1
or
set deviceconfig system ip-address 172.16.1.100 netmask 255.255.255.0 default-gateway 172.16.1.1
set deviceconfig system dns-setting servers primary 8.8.8.8
set deviceconfig system ntp-servers primary-ntp-server ntp-server-address 0.ca.pool.ntp.org
set deviceconfig system ip-address <Panorama-IP> netmask <netmask> default-gateway <gateway-IP> dns-setting servers primary <DNS-IP>
validate full
show jobs all
commit
then login GUI
Change admin password. Device >Administrators
Setup hostname, domain, and time zone. Device>Setup>Management
Add DNS server and NTP server IPs. Device>Setup>Services
Service route
License
Demo license activation:
1. Add VM Auth-Code in Support portal
2. GUI> Device > Licenses > Activate feature using authorization code.
Software -- for OS updates
Dynamic updates - For app, threat etc update
limit of VM
HA - Active/Passive only
10 interfaces
no vsys
vmotion is not allow
jumbo frame is not supported
LAG is on VM itself
Factory Reset method:
1.reboot from console
2. Enter "maint" mode
3. Choose "Factory Reset"
4. Wait for reload...
Ethernet Interface Types
1. tap mode - one port, IDS
2. L2 mode !!switch ports, optional VLAN interface to route traffic to other networks
3. V-wire -transparent FW, only two ports, IPS
4. L3 mode
5. HA
loopback interface
tunnel interface
subinterface
Network> VLANs
a broadcast domain, or bridge domain, contains multiple L2 interfaces, even L2 sub-interfaces are tagged differently.
Interface management profile -- service or IP filter
When configure interface IP Address, put ip address directly, no need to create address object.
Security policy
Intra-zone is allowed by default
Inter-zone is denied by default
Internet traffic to FW outside interface matches Intra-zone default policy (untrust to untrust). Create a rule near the top to block traffic to FW outside interface. GlobalProtect rule should be above it.
or create a explicit deny untrust-to untrust rule above intrazone-default rule
Create Zones - different type interface has different zone.
Create management profile for interfaces
Create objects for interface IPs
Create interfaces.
Create sub-interface if trunk
SNAT:
static
dynamic IP and port - PAT
dynamic IP
When create PAT:
Specify interface IP is optional.
DNAT:
source zone and destination are both Untrusted.
static
port forwarding
Security Policy.
use applications in policy, can use Application Filters (dynamic) or Application Groups (static)
application dependency (implicit, explicit)
Object: DBL (Dynamic block list) - New term: External Dynamic Lists
after created, use it in address section is Security Policy
Use NATed IP address in security policy for inbound access.
License:
Threat and Protection: Anti-virus, anti-spyware, vulnerabilities.
URL:URL filter
WildFire: malware analysis, PA cloud sandbox
WildFire Verdicts:
Benign: safe
Grayware: adware, spyware, and Browser Helper Objects (BHOs).
Phishing:
Malicious: Malware includes virus, worms, Trojans, rootkits, and botnets.
Content ID
Security Profiles:
Antivirus
Anti-Spyware
Vulnerabilities
Above three in threat log.
URL filtering
File Blocking
Data Filtering
DoS protection profile: flood protection and resource protection, then attach to Dos Protection Policy
Zone protection profile
User ID:
AD user agentLDAP user agent
captive portal
TS agent
PAN client
Group mapping, then group can be used in security policy
1. Create server profile, like ldap server profile.
2. User Identification > Group Mapping Setting
User Mapping (Agentless), for user-IP mapping, pull user login log via WMI
User Identification > User mapping > Palo Alto Networks User-ID Agent Setup > Server Monitor Account.
User Identification > User mapping > Palo Alto Networks User-ID Agent Setup > Server Monitor.
User Identification > User mapping > Server Monitoring.
How to Configure Agentless User-ID
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClGGCA0
show user user-ids match-user []
show user ip-user-mapping all
Authentication Profile refers a server profile (with Allow List), then be used in creating admin account or captive portal to actually authenticate user:
test authentication authentication-profile Auth-Profile username user1 password
Enter password :
Target vsys is not specified, user "user1" is assumed to be configured with a shared auth profile.
Do allow list check before sending out authentication request...
name "user1" is in group "all"
Authentication to LDAP server at 172.16.1.10 for user "user1"
Egress: 172.16.1.62
Type of authentication: plaintext
Starting LDAP connection...
Succeeded to create a session with LDAP server
DN sent to LDAP server: CN=user1,CN=Users,DC=lab,DC=local
User expires in days: never
Authentication succeeded for user "user1"
admin@Panorama>
Apply Decryption Policy
Wildfire
could service detect unknown threats, generate verdict:
Benign -- Allow
Grayware -- Allow
Phishing -- Deny
Malware -- Deny
1.QoS Profile (aka service-map)
Define BW usage or PQ for each class
2. QoS Policy (aka class-map)
Define what traffic assign to which class.
Qos policy processed after other policies.
3. Activate QoS on an interface (aka service-policy), assign QoS Profile
Network>QoS
============Log==============
1. Device > Server Profiles: SNMP trap, Email, Syslog and HTTP
2. For system, configuration etc, Device > Log Settings
3. For traffic related, Objects > Log forwarding
3.1 specify Log Type, Forward Method
if log forwarding profile is "default", it will be selected by all security policy automatically.
3.2. Assign the Log Forwarding profile to a Security Policy
VM-Series Plugin
download and install.
Save candidate configuration .snapshot.xml
Revert to running configuration running-config.xml
Reset Configuration
1. When admin password is known, and wants to keep
2. When admin password is known, and want to reset to factory default
3. When admin password is unknown
Device Certificate
show device-certificate status











Comments
Post a Comment