IKEv1
RFC describes DPD negotiation procedure and two new ISAKMP NOTIFY messages. Specifically, DPD is negotiated via an exchange of the DPD ISAKMP Vendor ID payload, which is sent in the ISAKMP MM messages 3 and 4 or ISAKMP AM messages 1 and 2. DPD Requests are sent as ISAKMP R-U-THERE messages and DPD Responses are sent as ISAKMP R-U-THERE-ACK messages.
ASA supports "semi-periodic" DPD only. I.e. they send R-U-THERE message to a peer if the peer was idle for
If the peer doesn't respond with the R-U-THERE-ACK the ASA starts retransmitting R-U-THERE messages every
Config:
Default is enabled
ASAv1# sh run all tunnel-group 203.0.113.2
tunnel-group 203.0.113.2 type ipsec-l2l
tunnel-group 203.0.113.2 general-attributes
default-group-policy DfltGrpPolicy
tunnel-group 203.0.113.2 ipsec-attributes
ikev1 pre-shared-key *****
peer-id-validate req
no chain
no ikev1 trust-point
isakmp keepalive threshold 10 retry 2
no ikev2 remote-authentication
no ikev2 local-authentication
ASA DPD uses keepalive command, but in FortiGate, they are different concepts.
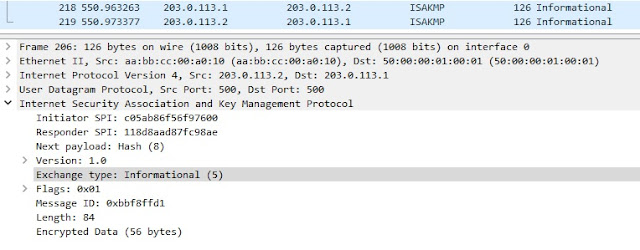
Jan 28 19:52:20 [IKEv1 DEBUG]Group = 203.0.113.1, IP = 203.0.113.1, Received keep-alive of type DPD R-U-THERE (seq number 0x2227aa60)
Jan 28 19:52:20 [IKEv1 DEBUG]Group = 203.0.113.1, IP = 203.0.113.1, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x2227aa60)
IKEv2
On Cisco VPN router, DPD is configured globally or in IKEv2 Profile
global default:
crypto ikev2 dpd 0 0 periodic
in IKEv2 Profile
crypto ikev2 profile IKEV2-PROFILE
match identity remote address 203.0.113.3 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local MYKEYS
dpd 10 3 periodic
R3#sh crypto ikev2 sa detail
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 203.0.113.1/4500 203.0.113.3/4500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/79 sec
CE id: 1017, Session-id: 58
Status Description: Negotiation done
Local spi: FA78392E99D34D5E Remote spi: D2BFFC45C7C0099E
Local id: 203.0.113.1
Remote id: 192.168.1.10
Local req msg id: 9 Remote req msg id: 0
Local next msg id: 9 Remote next msg id: 0
Local req queued: 9 Remote req queued: 0
Local window: 5 Remote window: 5
DPD configured for 10 seconds, retry 3
Fragmentation not configured.
Extended Authentication not configured.
NAT-T is detected outside
Cisco Trust Security SGT is disabled
Initiator of SA : Yes
IPv6 Crypto IKEv2 SA
In this test (one VPN router behind NAT device ), it is sending in UDP/4500
Fortigate
DPP uses IKE Phase1 message.
DPD does NOT keep the tunnel up.
It only checks if the other side is alive and resets if not.
Keepalive uses IPSEC (ESP) traffic, NOT IKE
GUI: Autokey Keep Alive
GUI: Autokey Keep Alive
Force traffic periodically to keep the tunnel established, even when no real user traffic exists.
Comments
Post a Comment