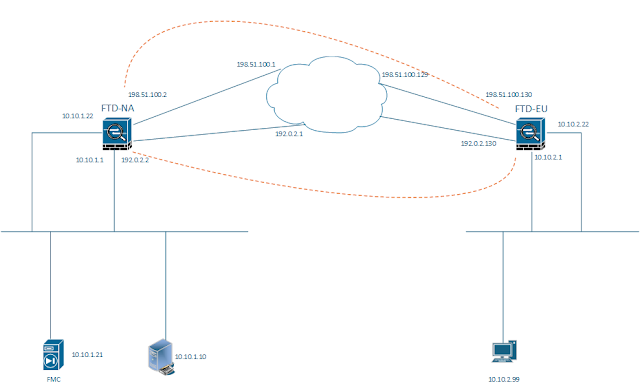
Lab Topology
Firepower 7.4.1
Both NA and EU sites have two ISPs, in sake of simplicity, two routed based site-to-site VPN tunnels are configured, which are ISP1 <>ISP1, ISP2<>ISP2.
Best Practice is to create one topology with backup VTI.
Alternately can create two topologies which do not use backup VTI.
For VPN failover, looks VPN DPD is sufficient to bring down vti causes VPN failover to backup tunnel, alternatively, we can setup vti interface path monitoring or using SLA,
With Path monitoring, it needs be configured on both side primary VTI interface.
FTD-NA:
FTD-EU
Before FTD-NA ISP1 is down:
Alternatively, we can use SLA for VPN failover
===
Another lab to test VPN Asymmetric routing
two VPN tunnels are configured on each FTD, on FTD1, VTI1 is the primary static route to peer LAN, on FTD2, VTI2 is the primary static route to peer LAN, there is symmetric routing, test result;
1. Ping from FTD1-LAN to FTD2-LAN uses VPN1 for both sending and receiving traffic
2. Ping from FTD2-LAN to FTD1-LAN uses VPN2 for both sending and receiving traffic
Conclusion:
FTD ignore the configured Asymmetric static routes are configured, traffic returns to the same VPN tunnel.
But ASA uses the Asymmetric static routes and route return traffic to another tunnel caused the traffic is dropped on FTD with "Drop-reason: (inspect-icmp-seq-num-not-matched) ", FTD can configure ECMP to fix this.
Alternative:
Use ECMP for two VTIs
ASA ECMP is not supported across multiple interfaces, are available only on the same interface
routed in








Comments
Post a Comment