Scenario:
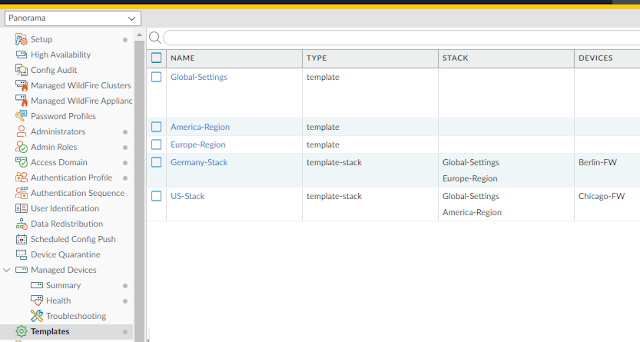
Panorama (192.168.1.252) manages Chicago-FW (192.168.1.254) and Burlin-FW (192.168.1.253)
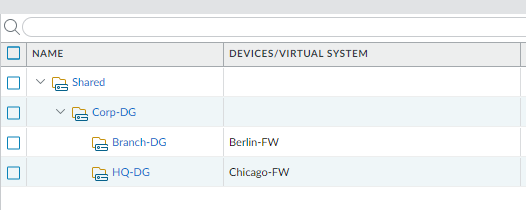
Device Group:
Goal:
AD user chicago-fw-admin (in AD group Chicago-FW-Admins) login Panorama can only configure HQ-DG and US-Stack.
AD user berlin-fw-admin (in AD group Berlin-FW-Admins) login Panorama can only configure Branch-DG and Germany-Stack.
Create Amdin Role
This example created two admin roles, but here they are same.
Panorama > Setup >
ISE settings:
Add PaloAlto dictionary
Policy > Policy Elements >Dictionaries > System > radius > RADIUS Vendors
https://docs.paloaltonetworks.com/resources/radius-dictionary.html
https://docs.paloaltonetworks.com/resources/radius-dictionary.html
Created Network device Profile
Add Panorama as a network device:
Create two Authorization Profiles:
Authorization Policies
===============
Packet capture















Comments
Post a Comment