ASA buffer logging is at Debugging Level, no debug is enabled
policy-based VPN is configured for host 10.0.10.100 to communicate to host 10.0.20.100
- when ping trigger VPN from VPC-ASA
No configuration issue, VPN tunnel is up
ASA log:
Palo System log:
Phase I (IKE) parameter mismatch:
ASA log:
Palo System log:
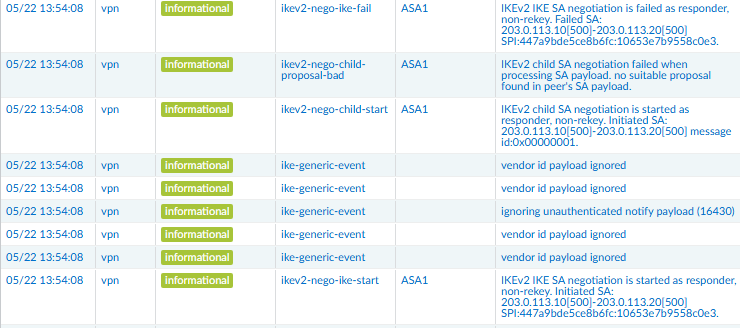
Phase II parameter mismatch
ASA:
Palo:
Pre-shared key mismatch
ASA log:
Palo System Log:
IKE lifetime mismatch, VPN is UP, Palo and ASA firewalls use their local configured IKE lifetime value generating IKE sa.
IPSEC lifetime mismatch, VPN is UP. Palo and ASA firewalls use their local configured IPSec lifetime value generating IPSec sa
ASA used to have default 1 hour IPSec lifetime, this lab ASA version is 9.16 (4), which has default 8 hours.
Note:
In ASA logs, phase I and Phase II parameter mismatch don't have much difference, except there are more IKE packets are received, from packet capture:
- phase I mismatch, only two IKE_SA_INIT packets
- phase II mismatch, two IKE_SA_INIT packets and multiple IKE_SA_Auth packets.
In Palo, phase I and Phase II parameter mismatch have different logs.
- when ping trigger VPN from VPC-Palo
ASA log:
we can see "IKEv2 SA UP", multiple received IKE packets, including IKE_SA_AUTH packets, however, no Error in the log.
we can see "IKEv2 SA UP", multiple received IKE packets, including IKE_SA_AUTH packets, however, no Error in the log.
Palo log:
Pre-shared key mismatch
ASA log:
Palo log:
========
IPSec PFS group
When pfs group 20 is configured on both ASA and Palo
group14 is default on ASA.
ASA:
Palo:
When pfs is not configured on ASA, but pfs group20 is configured on Palo, VPN tunnel is up (can be initiated from either ends)
ASA:
Palo:
Palo child sa shows group 20
When pfs group 20 is configured on ASA, but no pfs is configured on Palo, VPN tunnel is up (can be initiated from either ends).
Palo:
N/A
When pfs group 20 is configured on ASA, but pfs group14 is configured on Palo, VPN tunnel is up
ASA:
Palo:
N/A
Conclusion:
PFS mismatch is not an issue between Palo and ASA.
























Comments
Post a Comment