IKEv1 defines two phases:
* Phase 1 - on UDP/500, 6 packets, first 4 packets are in clear text, packet 5 and 6 are encrypted.
- Used for control plane
- Establish secure channel between peers
- Prove identities
- Negotiate data plane security settings
*Phase 2 - on UDP/500, 3 packets, Quick Mode, packets are encrypted.
- Used for data plane
- Transports the protected data
When both Phase1 and Phase 2 completed, data is encapsulated in ESP packet, and DPD is transferred in UDP/500
Phase1 packet 1:(Initiator)
has Initiator SPI, Responde SPI is empty. has phase1 proposal.
Phase 1 packet 2: (responder)
has both Initiator and Responder SPI filled up, has agreed phase1 proposal
Debug level 127
After packet 4, three keys are generated, NAT-T is determined
Phase 1 packet 5 & 6
Has Identification payload and Hash payload, used for identification and authentication, packets are encrypted, Pre-Shared-Key is verified here,
There are two items that are use to validate to each Peer that they both have the same PSK: the Identity Method and the Identity Hash
* Phase 1 - on UDP/500, 6 packets, first 4 packets are in clear text, packet 5 and 6 are encrypted.
- Used for control plane
- Establish secure channel between peers
- Prove identities
- Negotiate data plane security settings
*Phase 2 - on UDP/500, 3 packets, Quick Mode, packets are encrypted.
- Used for data plane
- Transports the protected data
When both Phase1 and Phase 2 completed, data is encapsulated in ESP packet, and DPD is transferred in UDP/500
Phase1 packet 1:(Initiator)
has Initiator SPI, Responde SPI is empty. has phase1 proposal.
debug level 127:
Dec 18
15:26:38 [IKEv1 DEBUG]Pitcher: received a key acquire message, spi 0x0
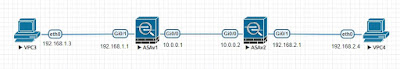
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, IKE
Initiator: New Phase 1, Intf inside, IKE Peer 10.0.0.2 local Proxy Address 192.168.1.0, remote Proxy
Address 192.168.2.0, Crypto map (MAP)
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing ISAKMP SA payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing NAT-Traversal VID ver 02
payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing NAT-Traversal VID ver 03 payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing NAT-Traversal VID ver RFC
payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing Fragmentation VID + extended
capabilities payload
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, IKE_DECODE
SENDING Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR
(13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 168
has both Initiator and Responder SPI filled up, has agreed phase1 proposal
Debug level 127
Dec 18 15:26:38 [IKEv1]IKE Receiver: Packet
received on 10.0.0.1:500 from 10.0.0.2:500
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, IKE_DECODE
RECEIVED Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR
(13) + NONE (0) total length : 128
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing SA payload
Dec 18 15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Oakley
proposal is acceptable
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing VID payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Received NAT-Traversal RFC VID
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing VID payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Received Fragmentation VID
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, IKE Peer included IKE fragmentation
capability flags: Main Mode: True
Aggressive Mode: True
Phase 1 packet 3 (Initiator)
Has DH Key Exchange payload, Nonce payload and NAT-D payload
A Nonce is simply a randomly generated number to use in key generation.The Nonce's are combined with the Pre-Shared-Key to create a Seed value for generating secret keys
Debug level 127
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing ke payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing nonce payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing Cisco Unity VID payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing xauth V6 VID payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Send IOS VID
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Constructing ASA spoofing IOS Vendor ID
payload (version: 1.0.0, capabilities: 20000001)
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing VID payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Send Altiga/Cisco VPN3000/Cisco ASA GW VID
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing NAT-Discovery payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, computing NAT Discovery hash
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, constructing NAT-Discovery payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, computing NAT Discovery hash
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, IKE_DECODE
SENDING Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + VENDOR
(13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NAT-D (20) + NAT-D (20) + NONE
(0) total length : 304
Phase 1 packet 4 (responder)
same content as packet 3Debug level 127
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, IKE_DECODE
RECEIVED Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + VENDOR
(13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NAT-D (20) + NAT-D (20) + NONE
(0) total length : 304
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing ke payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing ISA_KE payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing nonce payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing VID payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Received Cisco Unity client VID
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing VID payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Received xauth V6 VID
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing VID payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Processing VPN3000/ASA spoofing IOS Vendor
ID payload (version: 1.0.0, capabilities: 20000001)
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing VID payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Received Altiga/Cisco VPN3000/Cisco ASA GW
VID
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing NAT-Discovery payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, computing NAT Discovery hash
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, processing NAT-Discovery payload
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, computing NAT Discovery hash
Dec 18
15:26:38 [IKEv1]IP =
10.0.0.2, Connection landed on tunnel_group 10.0.0.2
Phase 1 packet 5 & 6
Has Identification payload and Hash payload, used for identification and authentication, packets are encrypted, Pre-Shared-Key is verified here,
There are two items that are use to validate to each Peer that they both have the same PSK: the Identity Method and the Identity Hash
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Generating keys for
Initiator...
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing ID payload
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing hash
payload
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Computing hash for
ISAKMP
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Constructing IOS keep alive payload:
proposal=32767/32767 sec.
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing dpd vid
payload
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, IKE_DECODE
SENDING Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + IOS
KEEPALIVE (128) + VENDOR (13) + NONE (0) total length : 96
Dec 18 15:26:38 [IKEv1]Group = 10.0.0.2, IP =
10.0.0.2, Automatic NAT Detection Status:
Remote end is NOT behind a NAT device
This end is NOT behind a NAT
device
Dec 18 15:26:38 [IKEv1]IKE Receiver: Packet
received on 10.0.0.1:500 from 10.0.0.2:500
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, IKE_DECODE
RECEIVED Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + IOS
KEEPALIVE (128) + VENDOR (13) + NONE (0) total length : 96
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing ID payload
Dec 18
15:26:38 [IKEv1 DECODE]Group = 10.0.0.2, IP = 10.0.0.2, ID_IPV4_ADDR ID
received
10.0.0.2
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing hash payload
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Computing hash for
ISAKMP
Dec 18
15:26:38 [IKEv1 DEBUG]IP = 10.0.0.2, Processing IOS keep alive payload:
proposal=32767/32767 sec.
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing VID payload
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Received DPD VID
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, Connection
landed on tunnel_group 10.0.0.2
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Oakley begin quick mode
Dec 18
15:26:38 [IKEv1 DECODE]Group = 10.0.0.2, IP = 10.0.0.2, IKE Initiator starting
QM: msg id = dd919b1a
Dec 18 15:26:38 [IKEv1]Group = 10.0.0.2, IP =
10.0.0.2, PHASE 1 COMPLETED
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, Keep-alive type
for this connection: DPD
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Starting P1 rekey timer:
73440 seconds.
Dec 18
15:26:38 [IKEv1]Group = 10.0.0.2, IP = 10.0.0.2, Add to IKEv1 Tunnel Table
succeeded for SA with logical ID 12288
Dec 18
15:26:38 [IKEv1]Group = 10.0.0.2, IP = 10.0.0.2, Add to IKEv1 MIB Table succeeded
for SA with logical ID 12288
3 Phase 2 Quick mode packets
Have phase 2 SA, Traffic Selector info.
Debug level 127
3 Phase 2 Quick mode packets
Have phase 2 SA, Traffic Selector info.
Debug level 127
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, IKE got SPI from key
engine: SPI = 0xb2e92848
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, oakley constructing quick mode
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing blank hash
payload
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing IPSec SA
payload
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing IPSec nonce
payload
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing proxy ID
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Transmitting Proxy Id:
Local subnet:
192.168.1.0 mask 255.255.255.0
Protocol 0 Port 0
Remote subnet: 192.168.2.0 Mask 255.255.255.0 Protocol 0 Port 0
Dec 18
15:26:38 [IKEv1 DECODE]Group = 10.0.0.2, IP = 10.0.0.2, IKE Initiator sending
Initial Contact
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing qm hash
payload
Dec 18
15:26:38 [IKEv1 DECODE]Group = 10.0.0.2, IP = 10.0.0.2, IKE Initiator sending
1st QM pkt: msg id = dd919b1a
Dec 18
15:26:38 [IKEv1]IP = 10.0.0.2, IKE_DECODE SENDING Message (msgid=dd919b1a) with
payloads : HDR + HASH (8) + SA (1) + NONCE (10) + ID (5) + ID (5) + NOTIFY (11)
+ NONE (0) total length : 200
Dec 18 15:26:38 [IKEv1]IKE Receiver: Packet
received on 10.0.0.1:500 from 10.0.0.2:500
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, IKE_DECODE
RECEIVED Message (msgid=dd919b1a) with payloads : HDR + HASH (8) + SA (1) +
NONCE (10) + ID (5) + ID (5) + NONE (0) total length : 172
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing hash payload
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing SA payload
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing nonce payload
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing ID payload
Dec 18
15:26:38 [IKEv1 DECODE]Group = 10.0.0.2, IP = 10.0.0.2, ID_IPV4_ADDR_SUBNET ID
received--192.168.1.0--255.255.255.0
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing ID payload
Dec 18
15:26:38 [IKEv1 DECODE]Group = 10.0.0.2, IP = 10.0.0.2, ID_IPV4_ADDR_SUBNET ID
received--192.168.2.0--255.255.255.0
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, loading all IPSEC SAs
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Generating Quick Mode
Key!
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Generating Quick Mode
Key!
Dec 18
15:26:38 [IKEv1]Group = 10.0.0.2, IP = 10.0.0.2, Security negotiation complete
for LAN-to-LAN Group (10.0.0.2)
Initiator, Inbound SPI = 0xb2e92848, Outbound SPI = 0x963662c7
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, oakley constructing
final quick mode
Dec 18 15:26:38 [IKEv1 DECODE]Group = 10.0.0.2, IP
= 10.0.0.2, IKE Initiator sending 3rd QM pkt: msg id = dd919b1a
Dec 18 15:26:38 [IKEv1]IP = 10.0.0.2, IKE_DECODE
SENDING Message (msgid=dd919b1a) with payloads : HDR + HASH (8) + NONE (0)
total length : 76
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, IKE got a KEY_ADD msg
for SA: SPI = 0x963662c7
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Pitcher: received
KEY_UPDATE, spi 0xb2e92848
Dec 18
15:26:38 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Starting P2 rekey timer:
24480 seconds.
Dec 18 15:26:38 [IKEv1]Group = 10.0.0.2, IP =
10.0.0.2, PHASE 2 COMPLETED (msgid=dd919b1a)
Dec 18
15:26:53 [IKEv1]IKE Receiver: Packet received on 10.0.0.1:500 from 10.0.0.2:500
Dec 18 15:26:53
[IKEv1]IP = 10.0.0.2, IKE_DECODE RECEIVED Message (msgid=dd6b3e08) with
payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
Dec 18
15:26:53 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing hash payload
Dec 18
15:26:53 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing notify
payload
Dec 18
15:26:53 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Received keep-alive of
type DPD R-U-THERE (seq number 0x2aaf99bd)
Dec 18
15:26:53 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Sending keep-alive of
type DPD R-U-THERE-ACK (seq number 0x2aaf99bd)
Dec 18
15:26:53 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing blank hash
payload
Dec 18
15:26:53 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing qm hash
payload
Dec 18
15:26:53 [IKEv1]IP = 10.0.0.2, IKE_DECODE SENDING Message (msgid=73748c8c) with
payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
Dec 18 15:27:03
[IKEv1]IKE Receiver: Packet received on 10.0.0.1:500 from 10.0.0.2:500
Dec 18
15:27:03 [IKEv1]IP = 10.0.0.2, IKE_DECODE RECEIVED Message (msgid=691aaa9b)
with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
Dec 18
15:27:03 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing hash payload
Dec 18
15:27:03 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing notify
payload
Dec 18
15:27:03 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, Received keep-alive of
type DPD R-U-THERE (seq number 0x2aaf99be)
Dec 18 15:27:03 [IKEv1 DEBUG]Group = 10.0.0.2,
IP = 10.0.0.2, Sending keep-alive of type DPD R-U-THERE-ACK (seq
number
0x2aaf99be)
Dec 18
15:27:03 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing blank hash
payload
Dec 18
15:27:03 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, constructing qm hash
payload
Dec 18
15:27:03 [IKEv1]IP = 10.0.0.2, IKE_DECODE SENDING Message (msgid=a3c98adf) with
payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
Dec 18
15:27:13 [IKEv1]IKE Receiver: Packet received on 10.0.0.1:500 from 10.0.0.2:500
Dec 18
15:27:13 [IKEv1]IP = 10.0.0.2, IKE_DECODE RECEIVED Message (msgid=d7833941)
with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
Dec 18
15:27:13 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing hash payload
Dec 18
15:27:13 [IKEv1 DEBUG]Group = 10.0.0.2, IP = 10.0.0.2, processing notify
payload




Comments
Post a Comment